mirror of
https://github.com/formbricks/formbricks.git
synced 2026-01-31 20:39:11 -06:00
Compare commits
1 Commits
fix-github
...
473-weekly
| Author | SHA1 | Date | |
|---|---|---|---|
|
|
eae5d67a2b |
@@ -1,56 +1,39 @@
|
||||
# See https://help.github.com/articles/ignoring-files/ for more about ignoring files.
|
||||
|
||||
# dependencies
|
||||
**/node_modules
|
||||
# **/node_modules
|
||||
.pnp
|
||||
.pnp.js
|
||||
.pnpm-store/
|
||||
|
||||
# testing
|
||||
**/coverage
|
||||
coverage
|
||||
|
||||
# next.js
|
||||
**/.next/
|
||||
**/out/
|
||||
**/.next
|
||||
**/out
|
||||
**/build
|
||||
|
||||
# node
|
||||
**/dist/
|
||||
**/dist
|
||||
|
||||
# misc
|
||||
**/.DS_Store
|
||||
.DS_Store
|
||||
*.pem
|
||||
Zone.Identifier
|
||||
|
||||
# debug
|
||||
npm-debug.log*
|
||||
yarn-debug.log*
|
||||
yarn-error.log*
|
||||
|
||||
# local env files
|
||||
**/.env
|
||||
**/.env.local
|
||||
**/.env.development.local
|
||||
**/.env.test.local
|
||||
**/.env.production.local
|
||||
!packages/database/.env
|
||||
!apps/web/.env
|
||||
|
||||
# build tools
|
||||
# turbo
|
||||
.turbo
|
||||
**/*vite.config.*.timestamp-*
|
||||
|
||||
# environment specific
|
||||
# nixos stuff
|
||||
.direnv
|
||||
|
||||
# Playwright
|
||||
/test-results/
|
||||
/playwright-report/
|
||||
/blob-report/
|
||||
/playwright/.cache/
|
||||
.vscode
|
||||
.github
|
||||
**/.turbo
|
||||
|
||||
# project specific
|
||||
packages/lib/uploads
|
||||
apps/web/public/js
|
||||
packages/database/migrations
|
||||
branch.json
|
||||
.env
|
||||
|
||||
@@ -130,9 +130,6 @@ AZUREAD_TENANT_ID=
|
||||
# OIDC_DISPLAY_NAME=
|
||||
# OIDC_SIGNING_ALGORITHM=
|
||||
|
||||
# Configure SAML SSO
|
||||
# SAML_DATABASE_URL=postgresql://postgres:postgres@localhost:5432/formbricks-saml
|
||||
|
||||
# Configure this when you want to ship JS & CSS files from a complete URL instead of the current domain
|
||||
# ASSET_PREFIX_URL=
|
||||
|
||||
|
||||
1
.github/workflows/sonarqube.yml
vendored
1
.github/workflows/sonarqube.yml
vendored
@@ -6,7 +6,6 @@ on:
|
||||
- main
|
||||
pull_request:
|
||||
types: [opened, synchronize, reopened]
|
||||
merge_group:
|
||||
permissions:
|
||||
contents: read
|
||||
jobs:
|
||||
|
||||
33
.github/workflows/tolgee.yml
vendored
33
.github/workflows/tolgee.yml
vendored
@@ -3,8 +3,7 @@ permissions:
|
||||
contents: read
|
||||
|
||||
on:
|
||||
pull_request:
|
||||
types: [closed]
|
||||
push:
|
||||
branches:
|
||||
- main
|
||||
|
||||
@@ -12,30 +11,10 @@ jobs:
|
||||
tag-production-keys:
|
||||
name: Tag Production Keys
|
||||
runs-on: ubuntu-latest
|
||||
if: github.event.pull_request.merged == true
|
||||
|
||||
steps:
|
||||
- name: Checkout repository
|
||||
uses: actions/checkout@v4
|
||||
with:
|
||||
fetch-depth: 0 # This ensures we get the full git history
|
||||
|
||||
- name: Get source branch name
|
||||
id: branch-name
|
||||
run: |
|
||||
# For PR merges, use the head ref from the pull request event
|
||||
SOURCE_BRANCH="${{ github.head_ref }}"
|
||||
|
||||
# Only remove username prefix if needed
|
||||
if [[ "$SOURCE_BRANCH" =~ ^[a-zA-Z0-9][a-zA-Z0-9-]+/ ]]; then
|
||||
PREFIX=${SOURCE_BRANCH%%/*}
|
||||
if [[ ! "$PREFIX" =~ ^(feature|fix|bugfix|hotfix|release|chore|docs|test|refactor|style|perf|build|ci|revert)$ ]]; then
|
||||
SOURCE_BRANCH=${SOURCE_BRANCH#*/}
|
||||
fi
|
||||
fi
|
||||
|
||||
echo "SOURCE_BRANCH=$SOURCE_BRANCH" >> $GITHUB_ENV
|
||||
echo "Detected source branch: $SOURCE_BRANCH"
|
||||
|
||||
- name: Setup Node.js
|
||||
uses: actions/setup-node@v4
|
||||
@@ -47,12 +26,13 @@ jobs:
|
||||
|
||||
- name: Tag Production Keys
|
||||
run: |
|
||||
BRANCH_NAME=${GITHUB_REF##*/}
|
||||
npx tolgee tag \
|
||||
--api-key ${{ secrets.TOLGEE_API_KEY }} \
|
||||
--filter-extracted \
|
||||
--filter-tag "draft:${SOURCE_BRANCH}" \
|
||||
--filter-tag "draft:${BRANCH_NAME}" \
|
||||
--tag production \
|
||||
--untag "draft:${SOURCE_BRANCH}"
|
||||
--untag "draft:${BRANCH_NAME}"
|
||||
|
||||
- name: Tag unused production keys as Deprecated
|
||||
run: |
|
||||
@@ -63,10 +43,11 @@ jobs:
|
||||
|
||||
- name: Tag unused draft:current-branch keys as Deprecated
|
||||
run: |
|
||||
BRANCH_NAME=${GITHUB_REF##*/}
|
||||
npx tolgee tag \
|
||||
--api-key ${{ secrets.TOLGEE_API_KEY }} \
|
||||
--filter-not-extracted --filter-tag "draft:${SOURCE_BRANCH}" \
|
||||
--tag deprecated --untag "draft:${SOURCE_BRANCH}"
|
||||
--filter-not-extracted --filter-tag "draft:${BRANCH_NAME}" \
|
||||
--tag deprecated --untag "draft:${BRANCH_NAME}"
|
||||
|
||||
- name: Sync with backup
|
||||
run: |
|
||||
|
||||
43
.gitignore
vendored
43
.gitignore
vendored
@@ -1,26 +1,25 @@
|
||||
# See https://help.github.com/articles/ignoring-files/ for more about ignoring files.
|
||||
|
||||
# dependencies
|
||||
**/node_modules
|
||||
node_modules
|
||||
.pnp
|
||||
.pnp.js
|
||||
.pnpm-store/
|
||||
|
||||
# testing
|
||||
**/coverage
|
||||
coverage
|
||||
|
||||
# next.js
|
||||
**/.next/
|
||||
**/out/
|
||||
**/build
|
||||
.next/
|
||||
out/
|
||||
build
|
||||
|
||||
# node
|
||||
**/dist/
|
||||
dist/
|
||||
|
||||
# misc
|
||||
**/.DS_Store
|
||||
.DS_Store
|
||||
*.pem
|
||||
Zone.Identifier
|
||||
|
||||
# debug
|
||||
npm-debug.log*
|
||||
@@ -28,29 +27,39 @@ yarn-debug.log*
|
||||
yarn-error.log*
|
||||
|
||||
# local env files
|
||||
**/.env
|
||||
**/.env.local
|
||||
**/.env.development.local
|
||||
**/.env.test.local
|
||||
**/.env.production.local
|
||||
.env
|
||||
.env.local
|
||||
.env.development.local
|
||||
.env.test.local
|
||||
.env.production.local
|
||||
!packages/database/.env
|
||||
!apps/web/.env
|
||||
|
||||
# build tools
|
||||
# turbo
|
||||
.turbo
|
||||
**/*vite.config.*.timestamp-*
|
||||
|
||||
# environment specific
|
||||
# nixos stuff
|
||||
.direnv
|
||||
|
||||
Zone.Identifier
|
||||
|
||||
# Playwright
|
||||
/test-results/
|
||||
/playwright-report/
|
||||
/blob-report/
|
||||
/playwright/.cache/
|
||||
|
||||
# project specific
|
||||
# uploads
|
||||
packages/lib/uploads
|
||||
|
||||
# Vite Timestamps
|
||||
*vite.config.*.timestamp-*
|
||||
|
||||
# js compiled assets
|
||||
apps/web/public/js
|
||||
|
||||
|
||||
packages/database/migrations
|
||||
|
||||
# tolgee
|
||||
branch.json
|
||||
@@ -1,2 +1 @@
|
||||
echo "{\"branchName\": \"$(git rev-parse --abbrev-ref HEAD)\"}" > ./branch.json
|
||||
prettier --write ./branch.json
|
||||
echo "{\"branchName\": \"$(git rev-parse --abbrev-ref HEAD)\"}" > ./branch.json
|
||||
1
.husky/post-commit
Normal file
1
.husky/post-commit
Normal file
@@ -0,0 +1 @@
|
||||
echo "{\"branchName\": \"$(git rev-parse --abbrev-ref HEAD)\"}" > ./branch.json
|
||||
@@ -3,19 +3,15 @@
|
||||
|
||||
# Load environment variables from .env files
|
||||
if [ -f .env ]; then
|
||||
set -a
|
||||
. .env
|
||||
set +a
|
||||
export $(cat .env | grep -v '#' | xargs)
|
||||
fi
|
||||
|
||||
pnpm lint-staged
|
||||
|
||||
# Run tolgee-pull if branch.json exists and NEXT_PUBLIC_TOLGEE_API_KEY is not set
|
||||
if [ -f branch.json ]; then
|
||||
if [ -z "$NEXT_PUBLIC_TOLGEE_API_KEY" ]; then
|
||||
echo "Skipping tolgee-pull: NEXT_PUBLIC_TOLGEE_API_KEY is not set"
|
||||
else
|
||||
pnpm run tolgee-pull
|
||||
git add packages/lib/messages
|
||||
fi
|
||||
fi
|
||||
if [ -z "$NEXT_PUBLIC_TOLGEE_API_KEY" ]; then
|
||||
echo "Skipping tolgee-pull: NEXT_PUBLIC_TOLGEE_API_KEY is not set"
|
||||
else
|
||||
pnpm run tolgee-pull
|
||||
git add packages/lib/messages
|
||||
fi
|
||||
|
||||
|
||||
1
.prettierignore
Normal file
1
.prettierignore
Normal file
@@ -0,0 +1 @@
|
||||
vercel.json
|
||||
@@ -13,7 +13,7 @@
|
||||
<h3 align="center">Formbricks</h3>
|
||||
|
||||
<p align="center">
|
||||
The Open Source Qualtrics Alternative
|
||||
Harvest user-insights, build irresistible experiences.
|
||||
<br />
|
||||
<a href="https://formbricks.com/">Website</a>
|
||||
</p>
|
||||
|
||||
3
apps/web/.gitignore
vendored
3
apps/web/.gitignore
vendored
@@ -48,6 +48,3 @@ uploads/
|
||||
|
||||
# Sentry Config File
|
||||
.sentryclirc
|
||||
|
||||
# SAML Preloaded Connections
|
||||
saml-connection/
|
||||
@@ -33,9 +33,6 @@ ENV CRON_SECRET="placeholder_for_cron_secret_of_64_chars_get_overwritten_at_runt
|
||||
ARG NEXT_PUBLIC_SENTRY_DSN
|
||||
ARG SENTRY_AUTH_TOKEN
|
||||
|
||||
# Increase Node.js memory limit
|
||||
# ENV NODE_OPTIONS="--max_old_space_size=4096"
|
||||
|
||||
# Set the working directory
|
||||
WORKDIR /app
|
||||
|
||||
@@ -44,17 +41,19 @@ WORKDIR /app
|
||||
# COPY --from=builder /app/out/json/ .
|
||||
# COPY --from=builder /app/out/pnpm-lock.yaml ./pnpm-lock.yaml
|
||||
|
||||
# Install the dependencies
|
||||
# RUN pnpm install
|
||||
|
||||
# Prepare the build
|
||||
COPY . .
|
||||
|
||||
# Create a .env file
|
||||
RUN touch apps/web/.env
|
||||
|
||||
# Install the dependencies
|
||||
RUN pnpm install
|
||||
|
||||
# Build the project
|
||||
RUN NODE_OPTIONS="--max_old_space_size=4096" pnpm build --filter=@formbricks/web...
|
||||
# RUN pnpm post-install --filter=@formbricks/web...
|
||||
RUN pnpm build --filter=@formbricks/web...
|
||||
|
||||
# Extract Prisma version
|
||||
RUN jq -r '.devDependencies.prisma' packages/database/package.json > /prisma_version.txt
|
||||
@@ -77,7 +76,6 @@ WORKDIR /home/nextjs
|
||||
COPY --from=installer /app/apps/web/next.config.mjs .
|
||||
COPY --from=installer /app/apps/web/package.json .
|
||||
# Leverage output traces to reduce image size
|
||||
|
||||
COPY --from=installer --chown=nextjs:nextjs /app/apps/web/.next/standalone ./
|
||||
COPY --from=installer --chown=nextjs:nextjs /app/apps/web/.next/static ./apps/web/.next/static
|
||||
COPY --from=installer --chown=nextjs:nextjs /app/apps/web/public ./apps/web/public
|
||||
@@ -107,11 +105,6 @@ ENV HOSTNAME "0.0.0.0"
|
||||
RUN mkdir -p /home/nextjs/apps/web/uploads/
|
||||
VOLUME /home/nextjs/apps/web/uploads/
|
||||
|
||||
# Prepare volume for SAML preloaded connection
|
||||
RUN mkdir -p /home/nextjs/apps/web/saml-connection
|
||||
VOLUME /home/nextjs/apps/web/saml-connection
|
||||
|
||||
CMD supercronic -quiet /app/docker/cronjobs & \
|
||||
(cd packages/database && npm run db:migrate:deploy) && \
|
||||
(cd packages/database && npm run db:create-saml-database:deploy) && \
|
||||
exec node apps/web/server.js
|
||||
|
||||
@@ -1,5 +1,4 @@
|
||||
import { AirtableWrapper } from "@/app/(app)/environments/[environmentId]/integrations/airtable/components/AirtableWrapper";
|
||||
import { getSurveys } from "@/app/(app)/environments/[environmentId]/integrations/lib/surveys";
|
||||
import { authOptions } from "@/modules/auth/lib/authOptions";
|
||||
import { getProjectPermissionByUserId } from "@/modules/ee/teams/lib/roles";
|
||||
import { getTeamPermissionFlags } from "@/modules/ee/teams/utils/teams";
|
||||
@@ -16,6 +15,7 @@ import { getIntegrations } from "@formbricks/lib/integration/service";
|
||||
import { getMembershipByUserIdOrganizationId } from "@formbricks/lib/membership/service";
|
||||
import { getAccessFlags } from "@formbricks/lib/membership/utils";
|
||||
import { getProjectByEnvironmentId } from "@formbricks/lib/project/service";
|
||||
import { getSurveys } from "@formbricks/lib/survey/service";
|
||||
import { findMatchingLocale } from "@formbricks/lib/utils/locale";
|
||||
import { TIntegrationItem } from "@formbricks/types/integration";
|
||||
import { TIntegrationAirtable } from "@formbricks/types/integration/airtable";
|
||||
|
||||
@@ -1,5 +1,4 @@
|
||||
import { GoogleSheetWrapper } from "@/app/(app)/environments/[environmentId]/integrations/google-sheets/components/GoogleSheetWrapper";
|
||||
import { getSurveys } from "@/app/(app)/environments/[environmentId]/integrations/lib/surveys";
|
||||
import { authOptions } from "@/modules/auth/lib/authOptions";
|
||||
import { getProjectPermissionByUserId } from "@/modules/ee/teams/lib/roles";
|
||||
import { getTeamPermissionFlags } from "@/modules/ee/teams/utils/teams";
|
||||
@@ -20,6 +19,7 @@ import { getIntegrations } from "@formbricks/lib/integration/service";
|
||||
import { getMembershipByUserIdOrganizationId } from "@formbricks/lib/membership/service";
|
||||
import { getAccessFlags } from "@formbricks/lib/membership/utils";
|
||||
import { getProjectByEnvironmentId } from "@formbricks/lib/project/service";
|
||||
import { getSurveys } from "@formbricks/lib/survey/service";
|
||||
import { findMatchingLocale } from "@formbricks/lib/utils/locale";
|
||||
import { TIntegrationGoogleSheets } from "@formbricks/types/integration/google-sheet";
|
||||
|
||||
|
||||
@@ -1,48 +0,0 @@
|
||||
import "server-only";
|
||||
import { Prisma } from "@prisma/client";
|
||||
import { cache as reactCache } from "react";
|
||||
import { prisma } from "@formbricks/database";
|
||||
import { cache } from "@formbricks/lib/cache";
|
||||
import { surveyCache } from "@formbricks/lib/survey/cache";
|
||||
import { selectSurvey } from "@formbricks/lib/survey/service";
|
||||
import { transformPrismaSurvey } from "@formbricks/lib/survey/utils";
|
||||
import { validateInputs } from "@formbricks/lib/utils/validate";
|
||||
import { ZId } from "@formbricks/types/common";
|
||||
import { DatabaseError } from "@formbricks/types/errors";
|
||||
import { TSurvey } from "@formbricks/types/surveys/types";
|
||||
|
||||
export const getSurveys = reactCache(
|
||||
async (environmentId: string): Promise<TSurvey[]> =>
|
||||
cache(
|
||||
async () => {
|
||||
validateInputs([environmentId, ZId]);
|
||||
|
||||
try {
|
||||
const surveysPrisma = await prisma.survey.findMany({
|
||||
where: {
|
||||
environmentId,
|
||||
status: {
|
||||
not: "completed",
|
||||
},
|
||||
},
|
||||
select: selectSurvey,
|
||||
orderBy: {
|
||||
updatedAt: "desc",
|
||||
},
|
||||
});
|
||||
|
||||
return surveysPrisma.map((surveyPrisma) => transformPrismaSurvey<TSurvey>(surveyPrisma));
|
||||
} catch (error) {
|
||||
if (error instanceof Prisma.PrismaClientKnownRequestError) {
|
||||
console.error(error);
|
||||
throw new DatabaseError(error.message);
|
||||
}
|
||||
throw error;
|
||||
}
|
||||
},
|
||||
[`getSurveys-${environmentId}`],
|
||||
{
|
||||
tags: [surveyCache.tag.byEnvironmentId(environmentId)],
|
||||
}
|
||||
)()
|
||||
);
|
||||
@@ -7,7 +7,6 @@ import {
|
||||
UNSUPPORTED_TYPES_BY_NOTION,
|
||||
} from "@/app/(app)/environments/[environmentId]/integrations/notion/constants";
|
||||
import NotionLogo from "@/images/notion.png";
|
||||
import { getQuestionTypes } from "@/modules/survey/lib/questions";
|
||||
import { Button } from "@/modules/ui/components/button";
|
||||
import { DropdownSelector } from "@/modules/ui/components/dropdown-selector";
|
||||
import { Label } from "@/modules/ui/components/label";
|
||||
@@ -20,6 +19,7 @@ import { useForm } from "react-hook-form";
|
||||
import toast from "react-hot-toast";
|
||||
import { getLocalizedValue } from "@formbricks/lib/i18n/utils";
|
||||
import { structuredClone } from "@formbricks/lib/pollyfills/structuredClone";
|
||||
import { getQuestionTypes } from "@formbricks/lib/utils/questions";
|
||||
import { replaceHeadlineRecall } from "@formbricks/lib/utils/recall";
|
||||
import { TIntegrationInput } from "@formbricks/types/integration";
|
||||
import {
|
||||
|
||||
@@ -1,4 +1,3 @@
|
||||
import { getSurveys } from "@/app/(app)/environments/[environmentId]/integrations/lib/surveys";
|
||||
import { NotionWrapper } from "@/app/(app)/environments/[environmentId]/integrations/notion/components/NotionWrapper";
|
||||
import { authOptions } from "@/modules/auth/lib/authOptions";
|
||||
import { getProjectPermissionByUserId } from "@/modules/ee/teams/lib/roles";
|
||||
@@ -22,6 +21,7 @@ import { getMembershipByUserIdOrganizationId } from "@formbricks/lib/membership/
|
||||
import { getAccessFlags } from "@formbricks/lib/membership/utils";
|
||||
import { getNotionDatabases } from "@formbricks/lib/notion/service";
|
||||
import { getProjectByEnvironmentId } from "@formbricks/lib/project/service";
|
||||
import { getSurveys } from "@formbricks/lib/survey/service";
|
||||
import { findMatchingLocale } from "@formbricks/lib/utils/locale";
|
||||
import { TIntegrationNotion, TIntegrationNotionDatabase } from "@formbricks/types/integration/notion";
|
||||
|
||||
|
||||
@@ -1,4 +1,3 @@
|
||||
import { getSurveys } from "@/app/(app)/environments/[environmentId]/integrations/lib/surveys";
|
||||
import { SlackWrapper } from "@/app/(app)/environments/[environmentId]/integrations/slack/components/SlackWrapper";
|
||||
import { authOptions } from "@/modules/auth/lib/authOptions";
|
||||
import { getProjectPermissionByUserId } from "@/modules/ee/teams/lib/roles";
|
||||
@@ -15,6 +14,7 @@ import { getIntegrationByType } from "@formbricks/lib/integration/service";
|
||||
import { getMembershipByUserIdOrganizationId } from "@formbricks/lib/membership/service";
|
||||
import { getAccessFlags } from "@formbricks/lib/membership/utils";
|
||||
import { getProjectByEnvironmentId } from "@formbricks/lib/project/service";
|
||||
import { getSurveys } from "@formbricks/lib/survey/service";
|
||||
import { findMatchingLocale } from "@formbricks/lib/utils/locale";
|
||||
import { TIntegrationSlack } from "@formbricks/types/integration/slack";
|
||||
|
||||
|
||||
@@ -1,7 +1,6 @@
|
||||
"use client";
|
||||
|
||||
import { RenderResponse } from "@/modules/analysis/components/SingleResponseCard/components/RenderResponse";
|
||||
import { VARIABLES_ICON_MAP, getQuestionIconMap } from "@/modules/survey/lib/questions";
|
||||
import { getSelectionColumn } from "@/modules/ui/components/data-table";
|
||||
import { ResponseBadges } from "@/modules/ui/components/response-badges";
|
||||
import { Tooltip, TooltipContent, TooltipProvider, TooltipTrigger } from "@/modules/ui/components/tooltip";
|
||||
@@ -13,6 +12,7 @@ import { getLocalizedValue } from "@formbricks/lib/i18n/utils";
|
||||
import { processResponseData } from "@formbricks/lib/responses";
|
||||
import { getContactIdentifier } from "@formbricks/lib/utils/contact";
|
||||
import { getFormattedDateTimeString } from "@formbricks/lib/utils/datetime";
|
||||
import { VARIABLES_ICON_MAP, getQuestionIconMap } from "@formbricks/lib/utils/questions";
|
||||
import { recallToHeadline } from "@formbricks/lib/utils/recall";
|
||||
import { TResponseTableData } from "@formbricks/types/responses";
|
||||
import { TSurvey, TSurveyQuestion } from "@formbricks/types/surveys/types";
|
||||
|
||||
@@ -51,9 +51,9 @@ export const HiddenFieldsSummary = ({ environment, questionSummary, locale }: Hi
|
||||
<div className="col-span-2 pl-4 md:pl-6">{t("common.response")}</div>
|
||||
<div className="px-4 md:px-6">{t("common.time")}</div>
|
||||
</div>
|
||||
{questionSummary.samples.slice(0, visibleResponses).map((response, idx) => (
|
||||
{questionSummary.samples.slice(0, visibleResponses).map((response) => (
|
||||
<div
|
||||
key={`${response.value}-${idx}`}
|
||||
key={response.value}
|
||||
className="grid grid-cols-4 items-center border-b border-slate-100 py-2 text-sm text-slate-800 md:text-base">
|
||||
<div className="pl-4 md:pl-6">
|
||||
{response.contact ? (
|
||||
|
||||
@@ -1,9 +1,9 @@
|
||||
"use client";
|
||||
|
||||
import { getQuestionTypes } from "@/modules/survey/lib/questions";
|
||||
import { useTranslate } from "@tolgee/react";
|
||||
import { InboxIcon } from "lucide-react";
|
||||
import type { JSX } from "react";
|
||||
import { getQuestionTypes } from "@formbricks/lib/utils/questions";
|
||||
import { recallToHeadline } from "@formbricks/lib/utils/recall";
|
||||
import { TSurvey, TSurveyQuestionSummary } from "@formbricks/types/surveys/types";
|
||||
|
||||
|
||||
@@ -1,10 +1,10 @@
|
||||
"use client";
|
||||
|
||||
import { getQuestionIcon } from "@/modules/survey/lib/questions";
|
||||
import { Tooltip, TooltipContent, TooltipProvider, TooltipTrigger } from "@/modules/ui/components/tooltip";
|
||||
import { useTranslate } from "@tolgee/react";
|
||||
import { TimerIcon } from "lucide-react";
|
||||
import { JSX } from "react";
|
||||
import { getQuestionIcon } from "@formbricks/lib/utils/questions";
|
||||
import { recallToHeadline } from "@formbricks/lib/utils/recall";
|
||||
import { TSurvey, TSurveyQuestionType, TSurveySummary } from "@formbricks/types/surveys/types";
|
||||
|
||||
|
||||
@@ -14,7 +14,6 @@ import {
|
||||
DropdownMenuItem,
|
||||
DropdownMenuTrigger,
|
||||
} from "@/modules/ui/components/dropdown-menu";
|
||||
import { Input } from "@/modules/ui/components/input";
|
||||
import { useTranslate } from "@tolgee/react";
|
||||
import clsx from "clsx";
|
||||
import { ChevronDown, ChevronUp, X } from "lucide-react";
|
||||
@@ -49,7 +48,6 @@ export const QuestionFilterComboBox = ({
|
||||
const [open, setOpen] = React.useState(false);
|
||||
const [openFilterValue, setOpenFilterValue] = React.useState<boolean>(false);
|
||||
const commandRef = React.useRef(null);
|
||||
const [searchQuery, setSearchQuery] = React.useState<string>("");
|
||||
const defaultLanguageCode = "default";
|
||||
useClickOutside(commandRef, () => setOpen(false));
|
||||
const { t } = useTranslate();
|
||||
@@ -75,12 +73,6 @@ export const QuestionFilterComboBox = ({
|
||||
(type === TSurveyQuestionTypeEnum.NPS || type === TSurveyQuestionTypeEnum.Rating) &&
|
||||
(filterValue === "Submitted" || filterValue === "Skipped");
|
||||
|
||||
const filteredOptions = options?.filter((o) =>
|
||||
(typeof o === "object" ? getLocalizedValue(o, defaultLanguageCode) : o)
|
||||
.toLowerCase()
|
||||
.includes(searchQuery.toLowerCase())
|
||||
);
|
||||
|
||||
return (
|
||||
<div className="inline-flex w-full flex-row">
|
||||
{filterOptions && filterOptions?.length <= 1 ? (
|
||||
@@ -168,21 +160,10 @@ export const QuestionFilterComboBox = ({
|
||||
{open && (
|
||||
<div className="animate-in bg-popover absolute top-0 z-10 max-h-52 w-full overflow-auto rounded-md bg-white outline-none">
|
||||
<CommandList>
|
||||
<div className="p-2">
|
||||
<Input
|
||||
type="text"
|
||||
autoFocus
|
||||
placeholder={t("common.search") + "..."}
|
||||
value={searchQuery}
|
||||
onChange={(e) => setSearchQuery(e.target.value)}
|
||||
className="w-full rounded-md border border-slate-300 p-2 text-sm focus:border-slate-300"
|
||||
/>
|
||||
</div>
|
||||
<CommandEmpty>{t("common.no_result_found")}</CommandEmpty>
|
||||
<CommandGroup>
|
||||
{filteredOptions?.map((o, index) => (
|
||||
{options?.map((o) => (
|
||||
<CommandItem
|
||||
key={`option-${typeof o === "object" ? getLocalizedValue(o, defaultLanguageCode) : o}-${index}`}
|
||||
onSelect={() => {
|
||||
!isMultiple
|
||||
? onChangeFilterComboBoxValue(
|
||||
|
||||
@@ -1,3 +0,0 @@
|
||||
import { GET } from "@/modules/ee/auth/saml/api/authorize/route";
|
||||
|
||||
export { GET };
|
||||
@@ -1,3 +0,0 @@
|
||||
import { POST } from "@/modules/ee/auth/saml/api/callback/route";
|
||||
|
||||
export { POST };
|
||||
@@ -1,3 +0,0 @@
|
||||
import { POST } from "@/modules/ee/auth/saml/api/token/route";
|
||||
|
||||
export { POST };
|
||||
@@ -1,3 +0,0 @@
|
||||
import { GET } from "@/modules/ee/auth/saml/api/userinfo/route";
|
||||
|
||||
export { GET };
|
||||
@@ -61,7 +61,6 @@ export const getSurveysForEnvironmentState = reactCache(
|
||||
displayLimit: true,
|
||||
displayOption: true,
|
||||
hiddenFields: true,
|
||||
isBackButtonHidden: true,
|
||||
triggers: {
|
||||
select: {
|
||||
actionClass: {
|
||||
|
||||
17
apps/web/app/health/error.tsx
Normal file
17
apps/web/app/health/error.tsx
Normal file
@@ -0,0 +1,17 @@
|
||||
"use client";
|
||||
|
||||
import { useTranslate } from "@tolgee/react";
|
||||
import { XCircleIcon } from "lucide-react";
|
||||
|
||||
const Error = ({ error }: { error: Error & { digest?: string } }) => {
|
||||
const { t } = useTranslate();
|
||||
return (
|
||||
<div className="mx-auto flex h-full max-w-xl flex-col items-center justify-center text-center">
|
||||
<XCircleIcon height={40} color="red" />
|
||||
<p className="text-md mt-4 font-bold text-zinc-900">{t("health.degraded")}</p>
|
||||
<p className="text-sm text-zinc-900">{error.message}</p>
|
||||
</div>
|
||||
);
|
||||
};
|
||||
|
||||
export default Error;
|
||||
54
apps/web/app/health/page.tsx
Normal file
54
apps/web/app/health/page.tsx
Normal file
@@ -0,0 +1,54 @@
|
||||
import { getTranslate } from "@/tolgee/server";
|
||||
import { BadgeCheckIcon } from "lucide-react";
|
||||
import { Metadata } from "next";
|
||||
import { prisma } from "@formbricks/database";
|
||||
|
||||
export const dynamic = "force-dynamic"; // no caching
|
||||
|
||||
export const metadata: Metadata = {
|
||||
robots: {
|
||||
index: false,
|
||||
follow: false,
|
||||
googleBot: {
|
||||
index: false,
|
||||
follow: false,
|
||||
},
|
||||
},
|
||||
};
|
||||
|
||||
const checkDatabaseConnection = async () => {
|
||||
try {
|
||||
await prisma.$queryRaw`SELECT 1`;
|
||||
} catch (e) {
|
||||
console.error("Database connection error:", e);
|
||||
throw new Error("Database could not be reached");
|
||||
}
|
||||
};
|
||||
|
||||
/* const checkS3Connection = async () => {
|
||||
if (!IS_S3_CONFIGURED) {
|
||||
// dont try connecting if not in use
|
||||
return;
|
||||
}
|
||||
try {
|
||||
await testS3BucketAccess();
|
||||
} catch (e) {
|
||||
throw new Error("S3 Bucket cannot be accessed");
|
||||
}
|
||||
}; */
|
||||
|
||||
const Page = async () => {
|
||||
const t = await getTranslate();
|
||||
await checkDatabaseConnection();
|
||||
// Skipping S3 check for now until it's fixed
|
||||
// await checkS3Connection();
|
||||
|
||||
return (
|
||||
<div className="mx-auto flex h-full max-w-xl flex-col items-center justify-center text-center">
|
||||
<BadgeCheckIcon height={40} color="green" />
|
||||
<p className="text-md mt-4 font-bold text-zinc-900">{t("health.healthy")}</p>
|
||||
</div>
|
||||
);
|
||||
};
|
||||
|
||||
export default Page;
|
||||
@@ -1,3 +0,0 @@
|
||||
export async function GET() {
|
||||
return Response.json({ status: "ok" });
|
||||
}
|
||||
@@ -7064,6 +7064,5 @@ export const previewSurvey = (projectName: string, t: TFnType) => {
|
||||
triggers: [],
|
||||
showLanguageSwitch: false,
|
||||
followUps: [],
|
||||
isBackButtonHidden: false,
|
||||
} as TSurvey;
|
||||
};
|
||||
|
||||
@@ -39,10 +39,7 @@ interface LoginFormProps {
|
||||
oidcOAuthEnabled: boolean;
|
||||
oidcDisplayName?: string;
|
||||
isMultiOrgEnabled: boolean;
|
||||
isSsoEnabled: boolean;
|
||||
samlSsoEnabled: boolean;
|
||||
samlTenant: string;
|
||||
samlProduct: string;
|
||||
isSSOEnabled: boolean;
|
||||
}
|
||||
|
||||
export const LoginForm = ({
|
||||
@@ -55,10 +52,7 @@ export const LoginForm = ({
|
||||
oidcOAuthEnabled,
|
||||
oidcDisplayName,
|
||||
isMultiOrgEnabled,
|
||||
isSsoEnabled,
|
||||
samlSsoEnabled,
|
||||
samlTenant,
|
||||
samlProduct,
|
||||
isSSOEnabled,
|
||||
}: LoginFormProps) => {
|
||||
const router = useRouter();
|
||||
const searchParams = useSearchParams();
|
||||
@@ -245,16 +239,13 @@ export const LoginForm = ({
|
||||
</Button>
|
||||
)}
|
||||
</form>
|
||||
{isSsoEnabled && (
|
||||
{isSSOEnabled && (
|
||||
<SSOOptions
|
||||
googleOAuthEnabled={googleOAuthEnabled}
|
||||
githubOAuthEnabled={githubOAuthEnabled}
|
||||
azureOAuthEnabled={azureOAuthEnabled}
|
||||
oidcOAuthEnabled={oidcOAuthEnabled}
|
||||
oidcDisplayName={oidcDisplayName}
|
||||
samlSsoEnabled={samlSsoEnabled}
|
||||
samlTenant={samlTenant}
|
||||
samlProduct={samlProduct}
|
||||
callbackUrl={callbackUrl}
|
||||
/>
|
||||
)}
|
||||
|
||||
@@ -1,10 +1,6 @@
|
||||
import { FormWrapper } from "@/modules/auth/components/form-wrapper";
|
||||
import { Testimonial } from "@/modules/auth/components/testimonial";
|
||||
import {
|
||||
getIsMultiOrgEnabled,
|
||||
getIsSamlSsoEnabled,
|
||||
getisSsoEnabled,
|
||||
} from "@/modules/ee/license-check/lib/utils";
|
||||
import { getIsMultiOrgEnabled, getIsSSOEnabled } from "@/modules/ee/license-check/lib/utils";
|
||||
import { Metadata } from "next";
|
||||
import {
|
||||
AZURE_OAUTH_ENABLED,
|
||||
@@ -14,9 +10,6 @@ import {
|
||||
OIDC_DISPLAY_NAME,
|
||||
OIDC_OAUTH_ENABLED,
|
||||
PASSWORD_RESET_DISABLED,
|
||||
SAML_OAUTH_ENABLED,
|
||||
SAML_PRODUCT,
|
||||
SAML_TENANT,
|
||||
SIGNUP_ENABLED,
|
||||
} from "@formbricks/lib/constants";
|
||||
import { LoginForm } from "./components/login-form";
|
||||
@@ -27,13 +20,7 @@ export const metadata: Metadata = {
|
||||
};
|
||||
|
||||
export const LoginPage = async () => {
|
||||
const [isMultiOrgEnabled, isSsoEnabled, isSamlSsoEnabled] = await Promise.all([
|
||||
getIsMultiOrgEnabled(),
|
||||
getisSsoEnabled(),
|
||||
getIsSamlSsoEnabled(),
|
||||
]);
|
||||
|
||||
const samlSsoEnabled = isSamlSsoEnabled && SAML_OAUTH_ENABLED;
|
||||
const [isMultiOrgEnabled, isSSOEnabled] = await Promise.all([getIsMultiOrgEnabled(), getIsSSOEnabled()]);
|
||||
return (
|
||||
<div className="grid min-h-screen w-full bg-gradient-to-tr from-slate-100 to-slate-50 lg:grid-cols-5">
|
||||
<div className="col-span-2 hidden lg:flex">
|
||||
@@ -51,10 +38,7 @@ export const LoginPage = async () => {
|
||||
oidcOAuthEnabled={OIDC_OAUTH_ENABLED}
|
||||
oidcDisplayName={OIDC_DISPLAY_NAME}
|
||||
isMultiOrgEnabled={isMultiOrgEnabled}
|
||||
isSsoEnabled={isSsoEnabled}
|
||||
samlSsoEnabled={samlSsoEnabled}
|
||||
samlTenant={SAML_TENANT}
|
||||
samlProduct={SAML_PRODUCT}
|
||||
isSSOEnabled={isSSOEnabled}
|
||||
/>
|
||||
</FormWrapper>
|
||||
</div>
|
||||
|
||||
@@ -53,11 +53,8 @@ interface SignupFormProps {
|
||||
emailVerificationDisabled: boolean;
|
||||
defaultOrganizationId?: string;
|
||||
defaultOrganizationRole?: TOrganizationRole;
|
||||
isSsoEnabled: boolean;
|
||||
samlSsoEnabled: boolean;
|
||||
isSSOEnabled: boolean;
|
||||
isTurnstileConfigured: boolean;
|
||||
samlTenant: string;
|
||||
samlProduct: string;
|
||||
}
|
||||
|
||||
export const SignupForm = ({
|
||||
@@ -75,11 +72,8 @@ export const SignupForm = ({
|
||||
emailVerificationDisabled,
|
||||
defaultOrganizationId,
|
||||
defaultOrganizationRole,
|
||||
isSsoEnabled,
|
||||
samlSsoEnabled,
|
||||
isSSOEnabled,
|
||||
isTurnstileConfigured,
|
||||
samlTenant,
|
||||
samlProduct,
|
||||
}: SignupFormProps) => {
|
||||
const [showLogin, setShowLogin] = useState(false);
|
||||
const searchParams = useSearchParams();
|
||||
@@ -272,16 +266,13 @@ export const SignupForm = ({
|
||||
</form>
|
||||
</FormProvider>
|
||||
)}
|
||||
{isSsoEnabled && (
|
||||
{isSSOEnabled && (
|
||||
<SSOOptions
|
||||
googleOAuthEnabled={googleOAuthEnabled}
|
||||
githubOAuthEnabled={githubOAuthEnabled}
|
||||
azureOAuthEnabled={azureOAuthEnabled}
|
||||
oidcOAuthEnabled={oidcOAuthEnabled}
|
||||
oidcDisplayName={oidcDisplayName}
|
||||
samlSsoEnabled={samlSsoEnabled}
|
||||
samlTenant={samlTenant}
|
||||
samlProduct={samlProduct}
|
||||
callbackUrl={callbackUrl}
|
||||
/>
|
||||
)}
|
||||
|
||||
@@ -1,10 +1,6 @@
|
||||
import { FormWrapper } from "@/modules/auth/components/form-wrapper";
|
||||
import { Testimonial } from "@/modules/auth/components/testimonial";
|
||||
import {
|
||||
getIsMultiOrgEnabled,
|
||||
getIsSamlSsoEnabled,
|
||||
getisSsoEnabled,
|
||||
} from "@/modules/ee/license-check/lib/utils";
|
||||
import { getIsMultiOrgEnabled, getIsSSOEnabled } from "@/modules/ee/license-check/lib/utils";
|
||||
import { notFound } from "next/navigation";
|
||||
import {
|
||||
AZURE_OAUTH_ENABLED,
|
||||
@@ -18,9 +14,6 @@ import {
|
||||
OIDC_DISPLAY_NAME,
|
||||
OIDC_OAUTH_ENABLED,
|
||||
PRIVACY_URL,
|
||||
SAML_OAUTH_ENABLED,
|
||||
SAML_PRODUCT,
|
||||
SAML_TENANT,
|
||||
SIGNUP_ENABLED,
|
||||
TERMS_URL,
|
||||
WEBAPP_URL,
|
||||
@@ -31,14 +24,7 @@ import { SignupForm } from "./components/signup-form";
|
||||
export const SignupPage = async ({ searchParams: searchParamsProps }) => {
|
||||
const searchParams = await searchParamsProps;
|
||||
const inviteToken = searchParams["inviteToken"] ?? null;
|
||||
const [isMultOrgEnabled, isSsoEnabled, isSamlSsoEnabled] = await Promise.all([
|
||||
getIsMultiOrgEnabled(),
|
||||
getisSsoEnabled(),
|
||||
getIsSamlSsoEnabled(),
|
||||
]);
|
||||
|
||||
const samlSsoEnabled = isSamlSsoEnabled && SAML_OAUTH_ENABLED;
|
||||
|
||||
const [isMultOrgEnabled, isSSOEnabled] = await Promise.all([getIsMultiOrgEnabled(), getIsSSOEnabled()]);
|
||||
const locale = await findMatchingLocale();
|
||||
if (!inviteToken && (!SIGNUP_ENABLED || !isMultOrgEnabled)) {
|
||||
notFound();
|
||||
@@ -67,11 +53,8 @@ export const SignupPage = async ({ searchParams: searchParamsProps }) => {
|
||||
emailFromSearchParams={emailFromSearchParams}
|
||||
defaultOrganizationId={DEFAULT_ORGANIZATION_ID}
|
||||
defaultOrganizationRole={DEFAULT_ORGANIZATION_ROLE}
|
||||
isSsoEnabled={isSsoEnabled}
|
||||
samlSsoEnabled={samlSsoEnabled}
|
||||
isSSOEnabled={isSSOEnabled}
|
||||
isTurnstileConfigured={IS_TURNSTILE_CONFIGURED}
|
||||
samlTenant={SAML_TENANT}
|
||||
samlProduct={SAML_PRODUCT}
|
||||
/>
|
||||
</FormWrapper>
|
||||
</div>
|
||||
|
||||
@@ -1,33 +0,0 @@
|
||||
import { responses } from "@/app/lib/api/response";
|
||||
import jackson from "@/modules/ee/auth/saml/lib/jackson";
|
||||
import { getIsSamlSsoEnabled } from "@/modules/ee/license-check/lib/utils";
|
||||
import type { OAuthReq } from "@boxyhq/saml-jackson";
|
||||
import { NextRequest, NextResponse } from "next/server";
|
||||
|
||||
export const GET = async (req: NextRequest) => {
|
||||
const jacksonInstance = await jackson();
|
||||
if (!jacksonInstance) {
|
||||
return responses.forbiddenResponse("SAML SSO is not enabled in your Formbricks license");
|
||||
}
|
||||
const { oauthController } = jacksonInstance;
|
||||
const searchParams = Object.fromEntries(req.nextUrl.searchParams);
|
||||
const isSamlSsoEnabled = await getIsSamlSsoEnabled();
|
||||
|
||||
if (!isSamlSsoEnabled) {
|
||||
return responses.forbiddenResponse("SAML SSO is not enabled in your Formbricks license");
|
||||
}
|
||||
|
||||
try {
|
||||
const { redirect_url } = await oauthController.authorize(searchParams as OAuthReq);
|
||||
|
||||
if (!redirect_url) {
|
||||
return responses.internalServerErrorResponse("Failed to get redirect URL");
|
||||
}
|
||||
|
||||
return NextResponse.redirect(redirect_url);
|
||||
} catch (err: unknown) {
|
||||
const errorMessage = err instanceof Error ? err.message : "An unknown error occurred";
|
||||
|
||||
return responses.internalServerErrorResponse(errorMessage);
|
||||
}
|
||||
};
|
||||
@@ -1,32 +0,0 @@
|
||||
import { responses } from "@/app/lib/api/response";
|
||||
import jackson from "@/modules/ee/auth/saml/lib/jackson";
|
||||
import { redirect } from "next/navigation";
|
||||
|
||||
interface SAMLCallbackBody {
|
||||
RelayState: string;
|
||||
SAMLResponse: string;
|
||||
}
|
||||
|
||||
export const POST = async (req: Request) => {
|
||||
const jacksonInstance = await jackson();
|
||||
if (!jacksonInstance) {
|
||||
return responses.forbiddenResponse("SAML SSO is not enabled in your Formbricks license");
|
||||
}
|
||||
const { oauthController } = jacksonInstance;
|
||||
|
||||
const formData = await req.formData();
|
||||
const body = Object.fromEntries(formData.entries());
|
||||
|
||||
const { RelayState, SAMLResponse } = body as unknown as SAMLCallbackBody;
|
||||
|
||||
const { redirect_url } = await oauthController.samlResponse({
|
||||
RelayState,
|
||||
SAMLResponse,
|
||||
});
|
||||
|
||||
if (!redirect_url) {
|
||||
return responses.internalServerErrorResponse("Failed to get redirect URL");
|
||||
}
|
||||
|
||||
return redirect(redirect_url);
|
||||
};
|
||||
@@ -1,18 +0,0 @@
|
||||
import { responses } from "@/app/lib/api/response";
|
||||
import jackson from "@/modules/ee/auth/saml/lib/jackson";
|
||||
import { OAuthTokenReq } from "@boxyhq/saml-jackson";
|
||||
|
||||
export const POST = async (req: Request) => {
|
||||
const jacksonInstance = await jackson();
|
||||
if (!jacksonInstance) {
|
||||
return responses.forbiddenResponse("SAML SSO is not enabled in your Formbricks license");
|
||||
}
|
||||
const { oauthController } = jacksonInstance;
|
||||
|
||||
const body = await req.formData();
|
||||
const formData = Object.fromEntries(body.entries());
|
||||
|
||||
const response = await oauthController.token(formData as unknown as OAuthTokenReq);
|
||||
|
||||
return Response.json(response);
|
||||
};
|
||||
@@ -1,87 +0,0 @@
|
||||
import { responses } from "@/app/lib/api/response";
|
||||
import { describe, expect, test, vi } from "vitest";
|
||||
import { extractAuthToken } from "./utils";
|
||||
|
||||
vi.mock("@/app/lib/api/response", () => ({
|
||||
responses: {
|
||||
unauthorizedResponse: vi.fn().mockReturnValue(new Error("Unauthorized")),
|
||||
},
|
||||
}));
|
||||
|
||||
describe("extractAuthToken", () => {
|
||||
test("extracts token from Authorization header with Bearer prefix", () => {
|
||||
const mockRequest = new Request("https://example.com", {
|
||||
headers: {
|
||||
authorization: "Bearer token123",
|
||||
},
|
||||
});
|
||||
|
||||
const token = extractAuthToken(mockRequest);
|
||||
expect(token).toBe("token123");
|
||||
});
|
||||
|
||||
test("extracts token from Authorization header with other prefix", () => {
|
||||
const mockRequest = new Request("https://example.com", {
|
||||
headers: {
|
||||
authorization: "Custom token123",
|
||||
},
|
||||
});
|
||||
|
||||
const token = extractAuthToken(mockRequest);
|
||||
expect(token).toBe("token123");
|
||||
});
|
||||
|
||||
test("extracts token from query parameter", () => {
|
||||
const mockRequest = new Request("https://example.com?access_token=token123");
|
||||
|
||||
const token = extractAuthToken(mockRequest);
|
||||
expect(token).toBe("token123");
|
||||
});
|
||||
|
||||
test("prioritizes Authorization header over query parameter", () => {
|
||||
const mockRequest = new Request("https://example.com?access_token=queryToken", {
|
||||
headers: {
|
||||
authorization: "Bearer headerToken",
|
||||
},
|
||||
});
|
||||
|
||||
const token = extractAuthToken(mockRequest);
|
||||
expect(token).toBe("headerToken");
|
||||
});
|
||||
|
||||
test("throws unauthorized error when no token is found", () => {
|
||||
const mockRequest = new Request("https://example.com");
|
||||
|
||||
expect(() => extractAuthToken(mockRequest)).toThrow("Unauthorized");
|
||||
expect(responses.unauthorizedResponse).toHaveBeenCalled();
|
||||
});
|
||||
|
||||
test("throws unauthorized error when Authorization header is empty", () => {
|
||||
const mockRequest = new Request("https://example.com", {
|
||||
headers: {
|
||||
authorization: "",
|
||||
},
|
||||
});
|
||||
|
||||
expect(() => extractAuthToken(mockRequest)).toThrow("Unauthorized");
|
||||
expect(responses.unauthorizedResponse).toHaveBeenCalled();
|
||||
});
|
||||
|
||||
test("throws unauthorized error when query parameter is empty", () => {
|
||||
const mockRequest = new Request("https://example.com?access_token=");
|
||||
|
||||
expect(() => extractAuthToken(mockRequest)).toThrow("Unauthorized");
|
||||
expect(responses.unauthorizedResponse).toHaveBeenCalled();
|
||||
});
|
||||
|
||||
test("handles Authorization header with only prefix", () => {
|
||||
const mockRequest = new Request("https://example.com", {
|
||||
headers: {
|
||||
authorization: "Bearer ",
|
||||
},
|
||||
});
|
||||
|
||||
expect(() => extractAuthToken(mockRequest)).toThrow("Unauthorized");
|
||||
expect(responses.unauthorizedResponse).toHaveBeenCalled();
|
||||
});
|
||||
});
|
||||
@@ -1,14 +0,0 @@
|
||||
import { responses } from "@/app/lib/api/response";
|
||||
|
||||
export const extractAuthToken = (req: Request) => {
|
||||
const authHeader = req.headers.get("authorization");
|
||||
const parts = (authHeader || "").split(" ");
|
||||
if (parts.length > 1) return parts[1];
|
||||
|
||||
// check for query param
|
||||
const params = new URL(req.url).searchParams;
|
||||
const accessToken = params.get("access_token");
|
||||
if (accessToken) return accessToken;
|
||||
|
||||
throw responses.unauthorizedResponse();
|
||||
};
|
||||
@@ -1,16 +0,0 @@
|
||||
import { responses } from "@/app/lib/api/response";
|
||||
import { extractAuthToken } from "@/modules/ee/auth/saml/api/userinfo/lib/utils";
|
||||
import jackson from "@/modules/ee/auth/saml/lib/jackson";
|
||||
|
||||
export const GET = async (req: Request) => {
|
||||
const jacksonInstance = await jackson();
|
||||
if (!jacksonInstance) {
|
||||
return responses.forbiddenResponse("SAML SSO is not enabled in your Formbricks license");
|
||||
}
|
||||
const { oauthController } = jacksonInstance;
|
||||
const token = extractAuthToken(req);
|
||||
|
||||
const user = await oauthController.userInfo(token);
|
||||
|
||||
return Response.json(user);
|
||||
};
|
||||
@@ -1,43 +0,0 @@
|
||||
"use server";
|
||||
|
||||
import { preloadConnection } from "@/modules/ee/auth/saml/lib/preload-connection";
|
||||
import { getIsSamlSsoEnabled } from "@/modules/ee/license-check/lib/utils";
|
||||
import type { IConnectionAPIController, IOAuthController, JacksonOption } from "@boxyhq/saml-jackson";
|
||||
import { SAML_AUDIENCE, SAML_DATABASE_URL, SAML_PATH, WEBAPP_URL } from "@formbricks/lib/constants";
|
||||
|
||||
const opts: JacksonOption = {
|
||||
externalUrl: WEBAPP_URL,
|
||||
samlAudience: SAML_AUDIENCE,
|
||||
samlPath: SAML_PATH,
|
||||
db: {
|
||||
engine: "sql",
|
||||
type: "postgres",
|
||||
url: SAML_DATABASE_URL,
|
||||
},
|
||||
};
|
||||
|
||||
declare global {
|
||||
var oauthController: IOAuthController | undefined;
|
||||
var connectionController: IConnectionAPIController | undefined;
|
||||
}
|
||||
|
||||
const g = global;
|
||||
|
||||
export default async function init() {
|
||||
if (!g.oauthController || !g.connectionController) {
|
||||
const isSamlSsoEnabled = await getIsSamlSsoEnabled();
|
||||
if (!isSamlSsoEnabled) return;
|
||||
|
||||
const ret = await (await import("@boxyhq/saml-jackson")).controllers(opts);
|
||||
|
||||
await preloadConnection(ret.connectionAPIController);
|
||||
|
||||
g.oauthController = ret.oauthController;
|
||||
g.connectionController = ret.connectionAPIController;
|
||||
}
|
||||
|
||||
return {
|
||||
oauthController: g.oauthController,
|
||||
connectionController: g.connectionController,
|
||||
};
|
||||
}
|
||||
@@ -1,73 +0,0 @@
|
||||
import { SAMLSSOConnectionWithEncodedMetadata, SAMLSSORecord } from "@boxyhq/saml-jackson";
|
||||
import { ConnectionAPIController } from "@boxyhq/saml-jackson/dist/controller/api";
|
||||
import fs from "fs/promises";
|
||||
import path from "path";
|
||||
import { SAML_PRODUCT, SAML_TENANT, SAML_XML_DIR, WEBAPP_URL } from "@formbricks/lib/constants";
|
||||
|
||||
const getPreloadedConnectionFile = async () => {
|
||||
const preloadedConnections = await fs.readdir(path.join(SAML_XML_DIR));
|
||||
const xmlFiles = preloadedConnections.filter((file) => file.endsWith(".xml"));
|
||||
if (xmlFiles.length === 0) {
|
||||
throw new Error("No preloaded connection file found");
|
||||
}
|
||||
return xmlFiles[0];
|
||||
};
|
||||
|
||||
const getPreloadedConnectionMetadata = async () => {
|
||||
const preloadedConnectionFile = await getPreloadedConnectionFile();
|
||||
|
||||
const preloadedConnectionMetadata = await fs.readFile(
|
||||
path.join(SAML_XML_DIR, preloadedConnectionFile),
|
||||
"utf8"
|
||||
);
|
||||
return preloadedConnectionMetadata;
|
||||
};
|
||||
|
||||
const getConnectionPayload = (metadata: string): SAMLSSOConnectionWithEncodedMetadata => {
|
||||
const encodedRawMetadata = Buffer.from(metadata, "utf8").toString("base64");
|
||||
|
||||
return {
|
||||
name: "SAML SSO",
|
||||
defaultRedirectUrl: `${WEBAPP_URL}/auth/login`,
|
||||
redirectUrl: [`${WEBAPP_URL}/*`],
|
||||
tenant: SAML_TENANT,
|
||||
product: SAML_PRODUCT,
|
||||
encodedRawMetadata,
|
||||
};
|
||||
};
|
||||
|
||||
export const preloadConnection = async (connectionController: ConnectionAPIController) => {
|
||||
try {
|
||||
const preloadedConnectionMetadata = await getPreloadedConnectionMetadata();
|
||||
|
||||
if (!preloadedConnectionMetadata) {
|
||||
console.log("No preloaded connection metadata found");
|
||||
return;
|
||||
}
|
||||
|
||||
const connections = await connectionController.getConnections({
|
||||
tenant: SAML_TENANT,
|
||||
product: SAML_PRODUCT,
|
||||
});
|
||||
|
||||
const existingConnection = connections[0];
|
||||
|
||||
const connection = getConnectionPayload(preloadedConnectionMetadata);
|
||||
let newConnection: SAMLSSORecord;
|
||||
try {
|
||||
newConnection = await connectionController.createSAMLConnection(connection);
|
||||
} catch (error) {
|
||||
throw new Error(`Metadata is not valid\n${error.message}`);
|
||||
}
|
||||
if (newConnection && existingConnection && newConnection.clientID !== existingConnection.clientID) {
|
||||
await connectionController.deleteConnections({
|
||||
clientID: existingConnection.clientID,
|
||||
clientSecret: existingConnection.clientSecret,
|
||||
product: existingConnection.product,
|
||||
tenant: existingConnection.tenant,
|
||||
});
|
||||
}
|
||||
} catch (error) {
|
||||
console.error("Error preloading connection:", error.message);
|
||||
}
|
||||
};
|
||||
@@ -1,110 +0,0 @@
|
||||
import { preloadConnection } from "@/modules/ee/auth/saml/lib/preload-connection";
|
||||
import { getIsSamlSsoEnabled } from "@/modules/ee/license-check/lib/utils";
|
||||
import { controllers } from "@boxyhq/saml-jackson";
|
||||
import { afterEach, beforeEach, describe, expect, test, vi } from "vitest";
|
||||
import { SAML_AUDIENCE, SAML_DATABASE_URL, SAML_PATH, WEBAPP_URL } from "@formbricks/lib/constants";
|
||||
import init from "../jackson";
|
||||
|
||||
vi.mock("@formbricks/lib/constants", () => ({
|
||||
SAML_AUDIENCE: "test-audience",
|
||||
SAML_DATABASE_URL: "test-db-url",
|
||||
SAML_PATH: "/test-path",
|
||||
WEBAPP_URL: "https://test-webapp-url.com",
|
||||
}));
|
||||
|
||||
vi.mock("@/modules/ee/license-check/lib/utils", () => ({
|
||||
getIsSamlSsoEnabled: vi.fn(),
|
||||
}));
|
||||
|
||||
vi.mock("@/modules/ee/auth/saml/lib/preload-connection", () => ({
|
||||
preloadConnection: vi.fn(),
|
||||
}));
|
||||
|
||||
vi.mock("@boxyhq/saml-jackson", () => ({
|
||||
controllers: vi.fn(),
|
||||
}));
|
||||
|
||||
describe("SAML Jackson Initialization", () => {
|
||||
const mockOAuthController = { name: "mockOAuthController" };
|
||||
const mockConnectionController = { name: "mockConnectionController" };
|
||||
|
||||
beforeEach(() => {
|
||||
vi.clearAllMocks();
|
||||
|
||||
global.oauthController = undefined;
|
||||
global.connectionController = undefined;
|
||||
|
||||
vi.mocked(controllers).mockResolvedValue({
|
||||
oauthController: mockOAuthController,
|
||||
connectionAPIController: mockConnectionController,
|
||||
} as any);
|
||||
});
|
||||
|
||||
afterEach(() => {
|
||||
vi.resetAllMocks();
|
||||
});
|
||||
|
||||
test("initialize controllers when SAML SSO is enabled", async () => {
|
||||
vi.mocked(getIsSamlSsoEnabled).mockResolvedValue(true);
|
||||
|
||||
const result = await init();
|
||||
|
||||
expect(getIsSamlSsoEnabled).toHaveBeenCalledTimes(1);
|
||||
|
||||
expect(controllers).toHaveBeenCalledWith({
|
||||
externalUrl: WEBAPP_URL,
|
||||
samlAudience: SAML_AUDIENCE,
|
||||
samlPath: SAML_PATH,
|
||||
db: {
|
||||
engine: "sql",
|
||||
type: "postgres",
|
||||
url: SAML_DATABASE_URL,
|
||||
},
|
||||
});
|
||||
|
||||
expect(preloadConnection).toHaveBeenCalledWith(mockConnectionController);
|
||||
|
||||
expect(global.oauthController).toBe(mockOAuthController);
|
||||
expect(global.connectionController).toBe(mockConnectionController);
|
||||
|
||||
expect(result).toEqual({
|
||||
oauthController: mockOAuthController,
|
||||
connectionController: mockConnectionController,
|
||||
});
|
||||
});
|
||||
|
||||
test("return early when SAML SSO is disabled", async () => {
|
||||
vi.mocked(getIsSamlSsoEnabled).mockResolvedValue(false);
|
||||
|
||||
const result = await init();
|
||||
|
||||
expect(getIsSamlSsoEnabled).toHaveBeenCalledTimes(1);
|
||||
|
||||
expect(controllers).not.toHaveBeenCalled();
|
||||
|
||||
expect(preloadConnection).not.toHaveBeenCalled();
|
||||
|
||||
expect(global.oauthController).toBeUndefined();
|
||||
expect(global.connectionController).toBeUndefined();
|
||||
|
||||
expect(result).toBeUndefined();
|
||||
});
|
||||
|
||||
test("reuse existing controllers if already initialized", async () => {
|
||||
global.oauthController = mockOAuthController as any;
|
||||
global.connectionController = mockConnectionController as any;
|
||||
|
||||
const result = await init();
|
||||
|
||||
expect(getIsSamlSsoEnabled).not.toHaveBeenCalled();
|
||||
|
||||
expect(controllers).not.toHaveBeenCalled();
|
||||
|
||||
expect(preloadConnection).not.toHaveBeenCalled();
|
||||
|
||||
expect(result).toEqual({
|
||||
oauthController: mockOAuthController,
|
||||
connectionController: mockConnectionController,
|
||||
});
|
||||
});
|
||||
});
|
||||
@@ -1,142 +0,0 @@
|
||||
import fs from "fs/promises";
|
||||
import path from "path";
|
||||
import { afterEach, beforeEach, describe, expect, test, vi } from "vitest";
|
||||
import { SAML_PRODUCT, SAML_TENANT, SAML_XML_DIR, WEBAPP_URL } from "@formbricks/lib/constants";
|
||||
import { preloadConnection } from "../preload-connection";
|
||||
|
||||
vi.mock("@formbricks/lib/constants", () => ({
|
||||
SAML_PRODUCT: "test-product",
|
||||
SAML_TENANT: "test-tenant",
|
||||
SAML_XML_DIR: "test-xml-dir",
|
||||
WEBAPP_URL: "https://test-webapp-url.com",
|
||||
}));
|
||||
|
||||
vi.mock("fs/promises", () => ({
|
||||
default: {
|
||||
readdir: vi.fn(),
|
||||
readFile: vi.fn(),
|
||||
},
|
||||
}));
|
||||
|
||||
vi.mock("path", () => ({
|
||||
default: {
|
||||
join: vi.fn(),
|
||||
},
|
||||
}));
|
||||
|
||||
vi.mock("@boxyhq/saml-jackson", () => ({
|
||||
SAMLSSOConnectionWithEncodedMetadata: vi.fn(),
|
||||
}));
|
||||
|
||||
vi.mock("@boxyhq/saml-jackson/dist/controller/api", () => ({
|
||||
ConnectionAPIController: vi.fn(),
|
||||
}));
|
||||
|
||||
describe("SAML Preload Connection", () => {
|
||||
const mockConnectionController = {
|
||||
getConnections: vi.fn(),
|
||||
createSAMLConnection: vi.fn(),
|
||||
deleteConnections: vi.fn(),
|
||||
};
|
||||
|
||||
const mockMetadata = "<EntityDescriptor>SAML Metadata</EntityDescriptor>";
|
||||
const mockEncodedMetadata = Buffer.from(mockMetadata, "utf8").toString("base64");
|
||||
|
||||
const mockExistingConnection = {
|
||||
clientID: "existing-client-id",
|
||||
clientSecret: "existing-client-secret",
|
||||
product: SAML_PRODUCT,
|
||||
tenant: SAML_TENANT,
|
||||
};
|
||||
|
||||
const mockNewConnection = {
|
||||
clientID: "new-client-id",
|
||||
clientSecret: "new-client-secret",
|
||||
};
|
||||
|
||||
beforeEach(() => {
|
||||
vi.clearAllMocks();
|
||||
|
||||
vi.mocked(path.join).mockImplementation((...args) => args.join("/"));
|
||||
|
||||
vi.mocked(fs.readdir).mockResolvedValue(["metadata.xml", "other-file.txt"] as any);
|
||||
|
||||
vi.mocked(fs.readFile).mockResolvedValue(mockMetadata as any);
|
||||
|
||||
mockConnectionController.getConnections.mockResolvedValue([mockExistingConnection]);
|
||||
|
||||
mockConnectionController.createSAMLConnection.mockResolvedValue(mockNewConnection);
|
||||
});
|
||||
|
||||
afterEach(() => {
|
||||
vi.resetAllMocks();
|
||||
});
|
||||
|
||||
test("preload connection from XML file", async () => {
|
||||
await preloadConnection(mockConnectionController as any);
|
||||
|
||||
expect(fs.readdir).toHaveBeenCalledWith(path.join(SAML_XML_DIR));
|
||||
|
||||
expect(fs.readFile).toHaveBeenCalledWith(path.join(SAML_XML_DIR, "metadata.xml"), "utf8");
|
||||
|
||||
expect(mockConnectionController.getConnections).toHaveBeenCalledWith({
|
||||
tenant: SAML_TENANT,
|
||||
product: SAML_PRODUCT,
|
||||
});
|
||||
|
||||
expect(mockConnectionController.createSAMLConnection).toHaveBeenCalledWith({
|
||||
name: "SAML SSO",
|
||||
defaultRedirectUrl: `${WEBAPP_URL}/auth/login`,
|
||||
redirectUrl: [`${WEBAPP_URL}/*`],
|
||||
tenant: SAML_TENANT,
|
||||
product: SAML_PRODUCT,
|
||||
encodedRawMetadata: mockEncodedMetadata,
|
||||
});
|
||||
|
||||
expect(mockConnectionController.deleteConnections).toHaveBeenCalledWith({
|
||||
clientID: mockExistingConnection.clientID,
|
||||
clientSecret: mockExistingConnection.clientSecret,
|
||||
product: mockExistingConnection.product,
|
||||
tenant: mockExistingConnection.tenant,
|
||||
});
|
||||
});
|
||||
|
||||
test("not delete existing connection if client IDs match", async () => {
|
||||
mockConnectionController.createSAMLConnection.mockResolvedValue({
|
||||
clientID: mockExistingConnection.clientID,
|
||||
});
|
||||
|
||||
await preloadConnection(mockConnectionController as any);
|
||||
|
||||
expect(mockConnectionController.deleteConnections).not.toHaveBeenCalled();
|
||||
});
|
||||
|
||||
test("handle case when no XML files are found", async () => {
|
||||
vi.mocked(fs.readdir).mockResolvedValue(["other-file.txt"] as any);
|
||||
|
||||
const consoleErrorSpy = vi.spyOn(console, "error");
|
||||
|
||||
await preloadConnection(mockConnectionController as any);
|
||||
|
||||
expect(consoleErrorSpy).toHaveBeenCalledWith(
|
||||
"Error preloading connection:",
|
||||
expect.stringContaining("No preloaded connection file found")
|
||||
);
|
||||
|
||||
expect(mockConnectionController.createSAMLConnection).not.toHaveBeenCalled();
|
||||
});
|
||||
|
||||
test("handle invalid metadata", async () => {
|
||||
const errorMessage = "Invalid metadata";
|
||||
mockConnectionController.createSAMLConnection.mockRejectedValue(new Error(errorMessage));
|
||||
|
||||
const consoleErrorSpy = vi.spyOn(console, "error");
|
||||
|
||||
await preloadConnection(mockConnectionController as any);
|
||||
|
||||
expect(consoleErrorSpy).toHaveBeenCalledWith(
|
||||
"Error preloading connection:",
|
||||
expect.stringContaining(errorMessage)
|
||||
);
|
||||
});
|
||||
});
|
||||
@@ -1,8 +1,7 @@
|
||||
import { getContactAttributes } from "@/modules/ee/contacts/lib/contact-attributes";
|
||||
import { getContact } from "@/modules/ee/contacts/lib/contacts";
|
||||
import { getTranslate } from "@/tolgee/server";
|
||||
import { getResponsesByContactId } from "@formbricks/lib/response/service";
|
||||
import { capitalizeFirstLetter } from "@formbricks/lib/utils/strings";
|
||||
import { getContact, getContactAttributes } from "../../lib/contacts";
|
||||
|
||||
export const AttributesSection = async ({ contactId }: { contactId: string }) => {
|
||||
const t = await getTranslate();
|
||||
|
||||
@@ -1,8 +1,7 @@
|
||||
import { authOptions } from "@/modules/auth/lib/authOptions";
|
||||
import { AttributesSection } from "@/modules/ee/contacts/[contactId]/components/attributes-section";
|
||||
import { DeleteContactButton } from "@/modules/ee/contacts/[contactId]/components/delete-contact-button";
|
||||
import { getContactAttributes } from "@/modules/ee/contacts/lib/contact-attributes";
|
||||
import { getContact } from "@/modules/ee/contacts/lib/contacts";
|
||||
import { getContact, getContactAttributes } from "@/modules/ee/contacts/lib/contacts";
|
||||
import { getContactIdentifier } from "@/modules/ee/contacts/lib/utils";
|
||||
import { getProjectPermissionByUserId } from "@/modules/ee/teams/lib/roles";
|
||||
import { getTeamPermissionFlags } from "@/modules/ee/teams/utils/teams";
|
||||
|
||||
@@ -1,12 +1,11 @@
|
||||
import { contactAttributeCache } from "@/lib/cache/contact-attribute";
|
||||
import { contactAttributeKeyCache } from "@/lib/cache/contact-attribute-key";
|
||||
import { getContactAttributeKeys } from "@/modules/ee/contacts/lib/contact-attribute-keys";
|
||||
import { hasEmailAttribute } from "@/modules/ee/contacts/lib/contact-attributes";
|
||||
import { prisma } from "@formbricks/database";
|
||||
import { MAX_ATTRIBUTE_CLASSES_PER_ENVIRONMENT } from "@formbricks/lib/constants";
|
||||
import { validateInputs } from "@formbricks/lib/utils/validate";
|
||||
import { ZId, ZString } from "@formbricks/types/common";
|
||||
import { TContactAttributes, ZContactAttributes } from "@formbricks/types/contact-attribute";
|
||||
import { getContactAttributeKeys } from "./contacts";
|
||||
|
||||
export const updateAttributes = async (
|
||||
contactId: string,
|
||||
@@ -25,7 +24,24 @@ export const updateAttributes = async (
|
||||
const [contactAttributeKeys, existingEmailAttribute] = await Promise.all([
|
||||
getContactAttributeKeys(environmentId),
|
||||
contactAttributesParam.email
|
||||
? hasEmailAttribute(contactAttributesParam.email, environmentId, contactId)
|
||||
? prisma.contactAttribute.findFirst({
|
||||
where: {
|
||||
AND: [
|
||||
{
|
||||
attributeKey: {
|
||||
key: "email",
|
||||
},
|
||||
value: contactAttributesParam.email,
|
||||
},
|
||||
{
|
||||
NOT: {
|
||||
contactId,
|
||||
},
|
||||
},
|
||||
],
|
||||
},
|
||||
select: { id: true },
|
||||
})
|
||||
: Promise.resolve(null),
|
||||
]);
|
||||
|
||||
|
||||
@@ -1,20 +0,0 @@
|
||||
import { contactAttributeKeyCache } from "@/lib/cache/contact-attribute-key";
|
||||
import { cache as reactCache } from "react";
|
||||
import { prisma } from "@formbricks/database";
|
||||
import { cache } from "@formbricks/lib/cache";
|
||||
import { TContactAttributeKey } from "@formbricks/types/contact-attribute-key";
|
||||
|
||||
export const getContactAttributeKeys = reactCache(
|
||||
(environmentId: string): Promise<TContactAttributeKey[]> =>
|
||||
cache(
|
||||
async () => {
|
||||
return await prisma.contactAttributeKey.findMany({
|
||||
where: { environmentId },
|
||||
});
|
||||
},
|
||||
[`getContactAttributeKeys-${environmentId}`],
|
||||
{
|
||||
tags: [contactAttributeKeyCache.tag.byEnvironmentId(environmentId)],
|
||||
}
|
||||
)()
|
||||
);
|
||||
@@ -1,92 +0,0 @@
|
||||
import { contactAttributeCache } from "@/lib/cache/contact-attribute";
|
||||
import { contactAttributeKeyCache } from "@/lib/cache/contact-attribute-key";
|
||||
import { Prisma } from "@prisma/client";
|
||||
import { cache as reactCache } from "react";
|
||||
import { prisma } from "@formbricks/database";
|
||||
import { cache } from "@formbricks/lib/cache";
|
||||
import { validateInputs } from "@formbricks/lib/utils/validate";
|
||||
import { ZId } from "@formbricks/types/common";
|
||||
import { TContactAttributes } from "@formbricks/types/contact-attribute";
|
||||
import { DatabaseError } from "@formbricks/types/errors";
|
||||
import { ZUserEmail } from "@formbricks/types/user";
|
||||
|
||||
const selectContactAttribute = {
|
||||
value: true,
|
||||
attributeKey: {
|
||||
select: {
|
||||
key: true,
|
||||
name: true,
|
||||
},
|
||||
},
|
||||
} satisfies Prisma.ContactAttributeSelect;
|
||||
|
||||
export const getContactAttributes = reactCache((contactId: string) =>
|
||||
cache(
|
||||
async () => {
|
||||
validateInputs([contactId, ZId]);
|
||||
|
||||
try {
|
||||
const prismaAttributes = await prisma.contactAttribute.findMany({
|
||||
where: {
|
||||
contactId,
|
||||
},
|
||||
select: selectContactAttribute,
|
||||
});
|
||||
|
||||
return prismaAttributes.reduce((acc, attr) => {
|
||||
acc[attr.attributeKey.key] = attr.value;
|
||||
return acc;
|
||||
}, {}) as TContactAttributes;
|
||||
} catch (error) {
|
||||
if (error instanceof Prisma.PrismaClientKnownRequestError) {
|
||||
throw new DatabaseError(error.message);
|
||||
}
|
||||
|
||||
throw error;
|
||||
}
|
||||
},
|
||||
[`getContactAttributes-${contactId}`],
|
||||
{
|
||||
tags: [contactAttributeCache.tag.byContactId(contactId)],
|
||||
}
|
||||
)()
|
||||
);
|
||||
|
||||
export const hasEmailAttribute = reactCache(
|
||||
async (email: string, environmentId: string, contactId: string): Promise<boolean> =>
|
||||
cache(
|
||||
async () => {
|
||||
validateInputs([email, ZUserEmail], [environmentId, ZId], [contactId, ZId]);
|
||||
|
||||
const contactAttribute = await prisma.contactAttribute.findFirst({
|
||||
where: {
|
||||
AND: [
|
||||
{
|
||||
attributeKey: {
|
||||
key: "email",
|
||||
environmentId,
|
||||
},
|
||||
value: email,
|
||||
},
|
||||
{
|
||||
NOT: {
|
||||
contactId,
|
||||
},
|
||||
},
|
||||
],
|
||||
},
|
||||
select: { id: true },
|
||||
});
|
||||
|
||||
return !!contactAttribute;
|
||||
},
|
||||
[`hasEmailAttribute-${email}-${environmentId}-${contactId}`],
|
||||
{
|
||||
tags: [
|
||||
contactAttributeKeyCache.tag.byEnvironmentIdAndKey(environmentId, "email"),
|
||||
contactAttributeCache.tag.byEnvironmentId(environmentId),
|
||||
contactAttributeCache.tag.byContactId(contactId),
|
||||
],
|
||||
}
|
||||
)()
|
||||
);
|
||||
@@ -9,6 +9,8 @@ import { cache } from "@formbricks/lib/cache";
|
||||
import { ITEMS_PER_PAGE } from "@formbricks/lib/constants";
|
||||
import { validateInputs } from "@formbricks/lib/utils/validate";
|
||||
import { ZId, ZOptionalNumber, ZOptionalString } from "@formbricks/types/common";
|
||||
import { TContactAttributes } from "@formbricks/types/contact-attribute";
|
||||
import { TContactAttributeKey } from "@formbricks/types/contact-attribute-key";
|
||||
import { DatabaseError, ValidationError } from "@formbricks/types/errors";
|
||||
import {
|
||||
TContact,
|
||||
@@ -37,6 +39,16 @@ const selectContact = {
|
||||
},
|
||||
} satisfies Prisma.ContactSelect;
|
||||
|
||||
const selectContactAttribute = {
|
||||
value: true,
|
||||
attributeKey: {
|
||||
select: {
|
||||
key: true,
|
||||
name: true,
|
||||
},
|
||||
},
|
||||
} satisfies Prisma.ContactAttributeSelect;
|
||||
|
||||
const buildContactWhereClause = (environmentId: string, search?: string): Prisma.ContactWhereInput => {
|
||||
const whereClause: Prisma.ContactWhereInput = { environmentId };
|
||||
|
||||
@@ -137,7 +149,6 @@ export const deleteContact = async (contactId: string): Promise<TContact | null>
|
||||
});
|
||||
|
||||
const contactUserId = contact.attributes.find((attr) => attr.attributeKey.key === "userId")?.value;
|
||||
const contactAttributes = contact.attributes;
|
||||
|
||||
contactCache.revalidate({
|
||||
id: contact.id,
|
||||
@@ -145,19 +156,6 @@ export const deleteContact = async (contactId: string): Promise<TContact | null>
|
||||
userId: contactUserId,
|
||||
});
|
||||
|
||||
for (const attr of contactAttributes) {
|
||||
contactAttributeCache.revalidate({
|
||||
contactId: contact.id,
|
||||
key: attr.attributeKey.key,
|
||||
environmentId: contact.environmentId,
|
||||
});
|
||||
|
||||
contactAttributeKeyCache.revalidate({
|
||||
environmentId: contact.environmentId,
|
||||
key: attr.attributeKey.key,
|
||||
});
|
||||
}
|
||||
|
||||
return contact;
|
||||
} catch (error) {
|
||||
if (error instanceof Prisma.PrismaClientKnownRequestError) {
|
||||
@@ -168,6 +166,54 @@ export const deleteContact = async (contactId: string): Promise<TContact | null>
|
||||
}
|
||||
};
|
||||
|
||||
export const getContactAttributes = reactCache((contactId: string) =>
|
||||
cache(
|
||||
async () => {
|
||||
validateInputs([contactId, ZId]);
|
||||
|
||||
try {
|
||||
const prismaAttributes = await prisma.contactAttribute.findMany({
|
||||
where: {
|
||||
contactId,
|
||||
},
|
||||
select: selectContactAttribute,
|
||||
});
|
||||
|
||||
// return convertPrismaContactAttributes(prismaAttributes);
|
||||
return prismaAttributes.reduce((acc, attr) => {
|
||||
acc[attr.attributeKey.key] = attr.value;
|
||||
return acc;
|
||||
}, {}) as TContactAttributes;
|
||||
} catch (error) {
|
||||
if (error instanceof Prisma.PrismaClientKnownRequestError) {
|
||||
throw new DatabaseError(error.message);
|
||||
}
|
||||
|
||||
throw error;
|
||||
}
|
||||
},
|
||||
[`getContactAttributes-${contactId}`],
|
||||
{
|
||||
tags: [contactAttributeCache.tag.byContactId(contactId)],
|
||||
}
|
||||
)()
|
||||
);
|
||||
|
||||
export const getContactAttributeKeys = reactCache(
|
||||
(environmentId: string): Promise<TContactAttributeKey[]> =>
|
||||
cache(
|
||||
async () => {
|
||||
return await prisma.contactAttributeKey.findMany({
|
||||
where: { environmentId },
|
||||
});
|
||||
},
|
||||
[`getContactAttributeKeys-${environmentId}`],
|
||||
{
|
||||
tags: [contactAttributeKeyCache.tag.byEnvironmentId(environmentId)],
|
||||
}
|
||||
)()
|
||||
);
|
||||
|
||||
export const createContactsFromCSV = async (
|
||||
csvData: Record<string, string>[],
|
||||
environmentId: string,
|
||||
|
||||
@@ -1,8 +1,7 @@
|
||||
import { contactCache } from "@/lib/cache/contact";
|
||||
import { authOptions } from "@/modules/auth/lib/authOptions";
|
||||
import { UploadContactsCSVButton } from "@/modules/ee/contacts/components/upload-contacts-button";
|
||||
import { getContactAttributeKeys } from "@/modules/ee/contacts/lib/contact-attribute-keys";
|
||||
import { getContacts } from "@/modules/ee/contacts/lib/contacts";
|
||||
import { getContactAttributeKeys, getContacts } from "@/modules/ee/contacts/lib/contacts";
|
||||
import { getIsContactsEnabled } from "@/modules/ee/license-check/lib/utils";
|
||||
import { getProjectPermissionByUserId } from "@/modules/ee/teams/lib/roles";
|
||||
import { getTeamPermissionFlags } from "@/modules/ee/teams/utils/teams";
|
||||
|
||||
@@ -1,6 +1,6 @@
|
||||
import { authOptions } from "@/modules/auth/lib/authOptions";
|
||||
import { ContactsSecondaryNavigation } from "@/modules/ee/contacts/components/contacts-secondary-navigation";
|
||||
import { getContactAttributeKeys } from "@/modules/ee/contacts/lib/contact-attribute-keys";
|
||||
import { getContactAttributeKeys } from "@/modules/ee/contacts/lib/contacts";
|
||||
import { SegmentTable } from "@/modules/ee/contacts/segments/components/segment-table";
|
||||
import { getSegments } from "@/modules/ee/contacts/segments/lib/segments";
|
||||
import { getIsContactsEnabled } from "@/modules/ee/license-check/lib/utils";
|
||||
|
||||
@@ -90,7 +90,6 @@ const fetchLicenseForE2ETesting = async (): Promise<{
|
||||
whitelabel: true,
|
||||
removeBranding: true,
|
||||
ai: true,
|
||||
saml: true,
|
||||
},
|
||||
lastChecked: currentTime,
|
||||
};
|
||||
@@ -157,7 +156,6 @@ export const getEnterpriseLicense = async (): Promise<{
|
||||
removeBranding: false,
|
||||
contacts: false,
|
||||
ai: false,
|
||||
saml: false,
|
||||
},
|
||||
lastChecked: new Date(),
|
||||
};
|
||||
@@ -363,7 +361,7 @@ export const getIsTwoFactorAuthEnabled = async (): Promise<boolean> => {
|
||||
return licenseFeatures.twoFactorAuth;
|
||||
};
|
||||
|
||||
export const getisSsoEnabled = async (): Promise<boolean> => {
|
||||
export const getIsSSOEnabled = async (): Promise<boolean> => {
|
||||
if (E2E_TESTING) {
|
||||
const previousResult = await fetchLicenseForE2ETesting();
|
||||
return previousResult && previousResult.features ? previousResult.features.sso : false;
|
||||
@@ -373,21 +371,6 @@ export const getisSsoEnabled = async (): Promise<boolean> => {
|
||||
return licenseFeatures.sso;
|
||||
};
|
||||
|
||||
export const getIsSamlSsoEnabled = async (): Promise<boolean> => {
|
||||
if (E2E_TESTING) {
|
||||
const previousResult = await fetchLicenseForE2ETesting();
|
||||
return previousResult && previousResult.features
|
||||
? previousResult.features.sso && previousResult.features.saml
|
||||
: false;
|
||||
}
|
||||
if (IS_FORMBRICKS_CLOUD) {
|
||||
return false;
|
||||
}
|
||||
const licenseFeatures = await getLicenseFeatures();
|
||||
if (!licenseFeatures) return false;
|
||||
return licenseFeatures.sso && licenseFeatures.saml;
|
||||
};
|
||||
|
||||
export const getIsOrganizationAIReady = async (billingPlan: Organization["billing"]["plan"]) => {
|
||||
if (!IS_AI_CONFIGURED) return false;
|
||||
if (E2E_TESTING) {
|
||||
|
||||
@@ -12,7 +12,6 @@ const ZEnterpriseLicenseFeatures = z.object({
|
||||
removeBranding: z.boolean(),
|
||||
twoFactorAuth: z.boolean(),
|
||||
sso: z.boolean(),
|
||||
saml: z.boolean(),
|
||||
ai: z.boolean(),
|
||||
});
|
||||
|
||||
|
||||
@@ -1,21 +0,0 @@
|
||||
"use server";
|
||||
|
||||
import { actionClient } from "@/lib/utils/action-client";
|
||||
import jackson from "@/modules/ee/auth/saml/lib/jackson";
|
||||
import { SAML_PRODUCT, SAML_TENANT } from "@formbricks/lib/constants";
|
||||
|
||||
export const doesSamlConnectionExistAction = actionClient.action(async () => {
|
||||
const jacksonInstance = await jackson();
|
||||
|
||||
if (!jacksonInstance) {
|
||||
return false;
|
||||
}
|
||||
|
||||
const { connectionController } = jacksonInstance;
|
||||
const connection = await connectionController.getConnections({
|
||||
product: SAML_PRODUCT,
|
||||
tenant: SAML_TENANT,
|
||||
});
|
||||
|
||||
return connection.length === 1;
|
||||
});
|
||||
@@ -8,7 +8,7 @@ import { useCallback, useEffect } from "react";
|
||||
import { FORMBRICKS_LOGGED_IN_WITH_LS } from "@formbricks/lib/localStorage";
|
||||
|
||||
interface AzureButtonProps {
|
||||
inviteUrl?: string;
|
||||
inviteUrl?: string | null;
|
||||
directRedirect?: boolean;
|
||||
lastUsed?: boolean;
|
||||
}
|
||||
|
||||
@@ -7,7 +7,7 @@ import { signIn } from "next-auth/react";
|
||||
import { FORMBRICKS_LOGGED_IN_WITH_LS } from "@formbricks/lib/localStorage";
|
||||
|
||||
interface GithubButtonProps {
|
||||
inviteUrl?: string;
|
||||
inviteUrl?: string | null;
|
||||
lastUsed?: boolean;
|
||||
}
|
||||
|
||||
|
||||
@@ -7,7 +7,7 @@ import { signIn } from "next-auth/react";
|
||||
import { FORMBRICKS_LOGGED_IN_WITH_LS } from "@formbricks/lib/localStorage";
|
||||
|
||||
interface GoogleButtonProps {
|
||||
inviteUrl?: string;
|
||||
inviteUrl?: string | null;
|
||||
lastUsed?: boolean;
|
||||
}
|
||||
|
||||
|
||||
@@ -7,7 +7,7 @@ import { useCallback, useEffect } from "react";
|
||||
import { FORMBRICKS_LOGGED_IN_WITH_LS } from "@formbricks/lib/localStorage";
|
||||
|
||||
interface OpenIdButtonProps {
|
||||
inviteUrl?: string;
|
||||
inviteUrl?: string | null;
|
||||
lastUsed?: boolean;
|
||||
directRedirect?: boolean;
|
||||
text?: string;
|
||||
|
||||
@@ -1,61 +0,0 @@
|
||||
"use client";
|
||||
|
||||
import { doesSamlConnectionExistAction } from "@/modules/ee/sso/actions";
|
||||
import { Button } from "@/modules/ui/components/button";
|
||||
import { useTranslate } from "@tolgee/react";
|
||||
import { LockIcon } from "lucide-react";
|
||||
import { signIn } from "next-auth/react";
|
||||
import { useState } from "react";
|
||||
import toast from "react-hot-toast";
|
||||
import { FORMBRICKS_LOGGED_IN_WITH_LS } from "@formbricks/lib/localStorage";
|
||||
|
||||
interface SamlButtonProps {
|
||||
inviteUrl?: string;
|
||||
lastUsed?: boolean;
|
||||
samlTenant: string;
|
||||
samlProduct: string;
|
||||
}
|
||||
|
||||
export const SamlButton = ({ inviteUrl, lastUsed, samlTenant, samlProduct }: SamlButtonProps) => {
|
||||
const { t } = useTranslate();
|
||||
const [isLoading, setIsLoading] = useState(false);
|
||||
|
||||
const handleLogin = async () => {
|
||||
if (typeof window !== "undefined") {
|
||||
localStorage.setItem(FORMBRICKS_LOGGED_IN_WITH_LS, "Saml");
|
||||
}
|
||||
setIsLoading(true);
|
||||
const doesSamlConnectionExist = await doesSamlConnectionExistAction();
|
||||
if (!doesSamlConnectionExist?.data) {
|
||||
toast.error(t("auth.saml_connection_error"));
|
||||
setIsLoading(false);
|
||||
return;
|
||||
}
|
||||
|
||||
signIn(
|
||||
"saml",
|
||||
{
|
||||
redirect: true,
|
||||
callbackUrl: inviteUrl ? inviteUrl : "/", // redirect after login to /
|
||||
},
|
||||
{
|
||||
tenant: samlTenant,
|
||||
product: samlProduct,
|
||||
}
|
||||
);
|
||||
};
|
||||
|
||||
return (
|
||||
<Button
|
||||
type="button"
|
||||
onClick={handleLogin}
|
||||
variant="secondary"
|
||||
className="relative w-full justify-center"
|
||||
loading={isLoading}>
|
||||
{t("auth.continue_with_saml")}
|
||||
|
||||
<LockIcon />
|
||||
{lastUsed && <span className="absolute right-3 text-xs opacity-50">{t("auth.last_used")}</span>}
|
||||
</Button>
|
||||
);
|
||||
};
|
||||
@@ -1,13 +1,10 @@
|
||||
"use client";
|
||||
|
||||
import { useTranslate } from "@tolgee/react";
|
||||
import { useEffect, useState } from "react";
|
||||
import { FORMBRICKS_LOGGED_IN_WITH_LS } from "@formbricks/lib/localStorage";
|
||||
import { AzureButton } from "./azure-button";
|
||||
import { GithubButton } from "./github-button";
|
||||
import { GoogleButton } from "./google-button";
|
||||
import { OpenIdButton } from "./open-id-button";
|
||||
import { SamlButton } from "./saml-button";
|
||||
|
||||
interface SSOOptionsProps {
|
||||
googleOAuthEnabled: boolean;
|
||||
@@ -16,9 +13,6 @@ interface SSOOptionsProps {
|
||||
oidcOAuthEnabled: boolean;
|
||||
oidcDisplayName?: string;
|
||||
callbackUrl: string;
|
||||
samlSsoEnabled: boolean;
|
||||
samlTenant: string;
|
||||
samlProduct: string;
|
||||
}
|
||||
|
||||
export const SSOOptions = ({
|
||||
@@ -28,42 +22,16 @@ export const SSOOptions = ({
|
||||
oidcOAuthEnabled,
|
||||
oidcDisplayName,
|
||||
callbackUrl,
|
||||
samlSsoEnabled,
|
||||
samlTenant,
|
||||
samlProduct,
|
||||
}: SSOOptionsProps) => {
|
||||
const { t } = useTranslate();
|
||||
const [lastLoggedInWith, setLastLoggedInWith] = useState("");
|
||||
|
||||
useEffect(() => {
|
||||
if (typeof window !== "undefined") {
|
||||
setLastLoggedInWith(localStorage.getItem(FORMBRICKS_LOGGED_IN_WITH_LS) || "");
|
||||
}
|
||||
}, []);
|
||||
|
||||
return (
|
||||
<div className="space-y-2">
|
||||
{googleOAuthEnabled && (
|
||||
<GoogleButton inviteUrl={callbackUrl} lastUsed={lastLoggedInWith === "Google"} />
|
||||
)}
|
||||
{githubOAuthEnabled && (
|
||||
<GithubButton inviteUrl={callbackUrl} lastUsed={lastLoggedInWith === "Github"} />
|
||||
)}
|
||||
{azureOAuthEnabled && <AzureButton inviteUrl={callbackUrl} lastUsed={lastLoggedInWith === "Azure"} />}
|
||||
{googleOAuthEnabled && <GoogleButton inviteUrl={callbackUrl} />}
|
||||
{githubOAuthEnabled && <GithubButton inviteUrl={callbackUrl} />}
|
||||
{azureOAuthEnabled && <AzureButton inviteUrl={callbackUrl} />}
|
||||
{oidcOAuthEnabled && (
|
||||
<OpenIdButton
|
||||
inviteUrl={callbackUrl}
|
||||
lastUsed={lastLoggedInWith === "OpenID"}
|
||||
text={t("auth.continue_with_oidc", { oidcDisplayName })}
|
||||
/>
|
||||
)}
|
||||
{samlSsoEnabled && (
|
||||
<SamlButton
|
||||
inviteUrl={callbackUrl}
|
||||
lastUsed={lastLoggedInWith === "Saml"}
|
||||
samlTenant={samlTenant}
|
||||
samlProduct={samlProduct}
|
||||
/>
|
||||
<OpenIdButton inviteUrl={callbackUrl} text={t("auth.continue_with_oidc", { oidcDisplayName })} />
|
||||
)}
|
||||
</div>
|
||||
);
|
||||
|
||||
@@ -15,7 +15,6 @@ import {
|
||||
OIDC_DISPLAY_NAME,
|
||||
OIDC_ISSUER,
|
||||
OIDC_SIGNING_ALGORITHM,
|
||||
WEBAPP_URL,
|
||||
} from "@formbricks/lib/constants";
|
||||
|
||||
export const getSSOProviders = () => [
|
||||
@@ -55,36 +54,6 @@ export const getSSOProviders = () => [
|
||||
};
|
||||
},
|
||||
},
|
||||
{
|
||||
id: "saml",
|
||||
name: "BoxyHQ SAML",
|
||||
type: "oauth" as const,
|
||||
version: "2.0",
|
||||
checks: ["pkce" as const, "state" as const],
|
||||
authorization: {
|
||||
url: `${WEBAPP_URL}/api/auth/saml/authorize`,
|
||||
params: {
|
||||
scope: "",
|
||||
response_type: "code",
|
||||
provider: "saml",
|
||||
},
|
||||
},
|
||||
token: `${WEBAPP_URL}/api/auth/saml/token`,
|
||||
userinfo: `${WEBAPP_URL}/api/auth/saml/userinfo`,
|
||||
profile(profile) {
|
||||
return {
|
||||
id: profile.id,
|
||||
email: profile.email,
|
||||
name: [profile.firstName, profile.lastName].filter(Boolean).join(" "),
|
||||
image: null,
|
||||
};
|
||||
},
|
||||
options: {
|
||||
clientId: "dummy",
|
||||
clientSecret: "dummy",
|
||||
},
|
||||
allowDangerousEmailAccountLinking: true,
|
||||
},
|
||||
];
|
||||
|
||||
export type { IdentityProvider };
|
||||
|
||||
@@ -1,7 +1,6 @@
|
||||
import { createBrevoCustomer } from "@/modules/auth/lib/brevo";
|
||||
import { getUserByEmail, updateUser } from "@/modules/auth/lib/user";
|
||||
import { createUser } from "@/modules/auth/lib/user";
|
||||
import { getIsSamlSsoEnabled, getisSsoEnabled } from "@/modules/ee/license-check/lib/utils";
|
||||
import type { IdentityProvider } from "@prisma/client";
|
||||
import type { Account } from "next-auth";
|
||||
import { prisma } from "@formbricks/database";
|
||||
@@ -13,25 +12,12 @@ import { findMatchingLocale } from "@formbricks/lib/utils/locale";
|
||||
import type { TUser, TUserNotificationSettings } from "@formbricks/types/user";
|
||||
|
||||
export const handleSSOCallback = async ({ user, account }: { user: TUser; account: Account }) => {
|
||||
const isSsoEnabled = await getisSsoEnabled();
|
||||
if (!isSsoEnabled) {
|
||||
return false;
|
||||
}
|
||||
|
||||
if (!user.email || account.type !== "oauth") {
|
||||
return false;
|
||||
}
|
||||
|
||||
let provider = account.provider.toLowerCase().replace("-", "") as IdentityProvider;
|
||||
|
||||
if (provider === "saml") {
|
||||
const isSamlSsoEnabled = await getIsSamlSsoEnabled();
|
||||
if (!isSamlSsoEnabled) {
|
||||
return false;
|
||||
}
|
||||
}
|
||||
|
||||
if (account.provider) {
|
||||
const provider = account.provider.toLowerCase().replace("-", "") as IdentityProvider;
|
||||
// check if accounts for this provider / account Id already exists
|
||||
const existingUserWithAccount = await prisma.user.findFirst({
|
||||
include: {
|
||||
|
||||
@@ -21,14 +21,14 @@ import { TSurvey } from "@formbricks/types/surveys/types";
|
||||
import { deleteWebhookAction, testEndpointAction, updateWebhookAction } from "../actions";
|
||||
import { TWebhookInput } from "../types/webhooks";
|
||||
|
||||
interface WebhookSettingsTabProps {
|
||||
interface ActionSettingsTabProps {
|
||||
webhook: Webhook;
|
||||
surveys: TSurvey[];
|
||||
setOpen: (v: boolean) => void;
|
||||
isReadOnly: boolean;
|
||||
}
|
||||
|
||||
export const WebhookSettingsTab = ({ webhook, surveys, setOpen, isReadOnly }: WebhookSettingsTabProps) => {
|
||||
export const WebhookSettingsTab = ({ webhook, surveys, setOpen, isReadOnly }: ActionSettingsTabProps) => {
|
||||
const { t } = useTranslate();
|
||||
const router = useRouter();
|
||||
const { register, handleSubmit } = useForm({
|
||||
@@ -219,7 +219,7 @@ export const WebhookSettingsTab = ({ webhook, surveys, setOpen, isReadOnly }: We
|
||||
|
||||
<div className="flex justify-between border-t border-slate-200 py-6">
|
||||
<div>
|
||||
{!isReadOnly && (
|
||||
{webhook.source === "user" && !isReadOnly && (
|
||||
<Button
|
||||
type="button"
|
||||
variant="destructive"
|
||||
|
||||
@@ -1,5 +1,5 @@
|
||||
import { SignupForm } from "@/modules/auth/signup/components/signup-form";
|
||||
import { getIsSamlSsoEnabled, getisSsoEnabled } from "@/modules/ee/license-check/lib/utils";
|
||||
import { getIsSSOEnabled } from "@/modules/ee/license-check/lib/utils";
|
||||
import { getTranslate } from "@/tolgee/server";
|
||||
import { Metadata } from "next";
|
||||
import {
|
||||
@@ -14,9 +14,6 @@ import {
|
||||
OIDC_DISPLAY_NAME,
|
||||
OIDC_OAUTH_ENABLED,
|
||||
PRIVACY_URL,
|
||||
SAML_OAUTH_ENABLED,
|
||||
SAML_PRODUCT,
|
||||
SAML_TENANT,
|
||||
TERMS_URL,
|
||||
WEBAPP_URL,
|
||||
} from "@formbricks/lib/constants";
|
||||
@@ -29,11 +26,7 @@ export const metadata: Metadata = {
|
||||
|
||||
export const SignupPage = async () => {
|
||||
const locale = await findMatchingLocale();
|
||||
|
||||
const [isSsoEnabled, isSamlSsoEnabled] = await Promise.all([getisSsoEnabled(), getIsSamlSsoEnabled()]);
|
||||
|
||||
const samlSsoEnabled = isSamlSsoEnabled && SAML_OAUTH_ENABLED;
|
||||
|
||||
const isSSOEnabled = await getIsSSOEnabled();
|
||||
const t = await getTranslate();
|
||||
return (
|
||||
<div className="flex flex-col items-center">
|
||||
@@ -54,11 +47,8 @@ export const SignupPage = async () => {
|
||||
userLocale={locale}
|
||||
defaultOrganizationId={DEFAULT_ORGANIZATION_ID}
|
||||
defaultOrganizationRole={DEFAULT_ORGANIZATION_ROLE}
|
||||
isSsoEnabled={isSsoEnabled}
|
||||
samlSsoEnabled={samlSsoEnabled}
|
||||
isSSOEnabled={isSSOEnabled}
|
||||
isTurnstileConfigured={IS_TURNSTILE_CONFIGURED}
|
||||
samlTenant={SAML_TENANT}
|
||||
samlProduct={SAML_PRODUCT}
|
||||
/>
|
||||
</div>
|
||||
);
|
||||
|
||||
@@ -1,11 +1,5 @@
|
||||
"use client";
|
||||
|
||||
import {
|
||||
getCXQuestionTypes,
|
||||
getQuestionDefaults,
|
||||
getQuestionTypes,
|
||||
universalQuestionPresets,
|
||||
} from "@/modules/survey/lib/questions";
|
||||
import { useAutoAnimate } from "@formkit/auto-animate/react";
|
||||
import { createId } from "@paralleldrive/cuid2";
|
||||
import { Project } from "@prisma/client";
|
||||
@@ -14,6 +8,12 @@ import { useTranslate } from "@tolgee/react";
|
||||
import { PlusIcon } from "lucide-react";
|
||||
import { useState } from "react";
|
||||
import { cn } from "@formbricks/lib/cn";
|
||||
import {
|
||||
getCXQuestionTypes,
|
||||
getQuestionDefaults,
|
||||
getQuestionTypes,
|
||||
universalQuestionPresets,
|
||||
} from "@formbricks/lib/utils/questions";
|
||||
|
||||
interface AddQuestionButtonProps {
|
||||
addQuestion: (question: any) => void;
|
||||
|
||||
@@ -1,11 +1,5 @@
|
||||
"use client";
|
||||
|
||||
import {
|
||||
getCXQuestionNameMap,
|
||||
getQuestionDefaults,
|
||||
getQuestionIconMap,
|
||||
getQuestionNameMap,
|
||||
} from "@/modules/survey/lib/questions";
|
||||
import { Button } from "@/modules/ui/components/button";
|
||||
import { ConfirmationModal } from "@/modules/ui/components/confirmation-modal";
|
||||
import {
|
||||
@@ -23,6 +17,12 @@ import { Project } from "@prisma/client";
|
||||
import { useTranslate } from "@tolgee/react";
|
||||
import { ArrowDownIcon, ArrowUpIcon, CopyIcon, EllipsisIcon, TrashIcon } from "lucide-react";
|
||||
import { useState } from "react";
|
||||
import {
|
||||
getCXQuestionNameMap,
|
||||
getQuestionDefaults,
|
||||
getQuestionIconMap,
|
||||
getQuestionNameMap,
|
||||
} from "@formbricks/lib/utils/questions";
|
||||
import {
|
||||
TSurvey,
|
||||
TSurveyEndScreenCard,
|
||||
|
||||
@@ -2,7 +2,6 @@
|
||||
|
||||
import { LogicEditorActions } from "@/modules/survey/editor/components/logic-editor-actions";
|
||||
import { LogicEditorConditions } from "@/modules/survey/editor/components/logic-editor-conditions";
|
||||
import { getQuestionIconMap } from "@/modules/survey/lib/questions";
|
||||
import {
|
||||
Select,
|
||||
SelectContent,
|
||||
@@ -14,6 +13,7 @@ import { useTranslate } from "@tolgee/react";
|
||||
import { ArrowRightIcon } from "lucide-react";
|
||||
import { ReactElement, useMemo } from "react";
|
||||
import { getLocalizedValue } from "@formbricks/lib/i18n/utils";
|
||||
import { getQuestionIconMap } from "@formbricks/lib/utils/questions";
|
||||
import { TSurvey, TSurveyLogic, TSurveyQuestion } from "@formbricks/types/surveys/types";
|
||||
|
||||
interface LogicEditorProps {
|
||||
|
||||
@@ -18,7 +18,6 @@ import { PictureSelectionForm } from "@/modules/survey/editor/components/picture
|
||||
import { RankingQuestionForm } from "@/modules/survey/editor/components/ranking-question-form";
|
||||
import { RatingQuestionForm } from "@/modules/survey/editor/components/rating-question-form";
|
||||
import { formatTextWithSlashes } from "@/modules/survey/editor/lib/utils";
|
||||
import { getQuestionIconMap, getTSurveyQuestionTypeEnumName } from "@/modules/survey/lib/questions";
|
||||
import { Label } from "@/modules/ui/components/label";
|
||||
import { Switch } from "@/modules/ui/components/switch";
|
||||
import { useSortable } from "@dnd-kit/sortable";
|
||||
@@ -30,6 +29,7 @@ import { useTranslate } from "@tolgee/react";
|
||||
import { ChevronDownIcon, ChevronRightIcon, GripIcon } from "lucide-react";
|
||||
import { useState } from "react";
|
||||
import { cn } from "@formbricks/lib/cn";
|
||||
import { getQuestionIconMap, getTSurveyQuestionTypeEnumName } from "@formbricks/lib/utils/questions";
|
||||
import { recallToHeadline } from "@formbricks/lib/utils/recall";
|
||||
import {
|
||||
TI18nString,
|
||||
|
||||
@@ -205,10 +205,6 @@ export const ResponseOptionsCard = ({
|
||||
}
|
||||
};
|
||||
|
||||
const handleHideBackButtonToggle = () => {
|
||||
setLocalSurvey({ ...localSurvey, isBackButtonHidden: !localSurvey.isBackButtonHidden });
|
||||
};
|
||||
|
||||
useEffect(() => {
|
||||
if (!!localSurvey.surveyClosedMessage) {
|
||||
setSurveyClosedMessage({
|
||||
@@ -519,13 +515,6 @@ export const ResponseOptionsCard = ({
|
||||
</AdvancedOptionToggle>
|
||||
</>
|
||||
)}
|
||||
<AdvancedOptionToggle
|
||||
htmlId="hideBackButton"
|
||||
isChecked={localSurvey.isBackButtonHidden}
|
||||
onToggle={handleHideBackButtonToggle}
|
||||
title={t("environments.surveys.edit.hide_back_button")}
|
||||
description={t("environments.surveys.edit.hide_back_button_description")}
|
||||
/>
|
||||
</div>
|
||||
</Collapsible.CollapsibleContent>
|
||||
</Collapsible.Root>
|
||||
|
||||
@@ -1,5 +1,4 @@
|
||||
import { TriggerUpdate } from "@/modules/survey/editor/types/survey-trigger";
|
||||
import { getQuestionTypes } from "@/modules/survey/lib/questions";
|
||||
import { TComboboxGroupedOption, TComboboxOption } from "@/modules/ui/components/input-combo-box";
|
||||
import { ActionClass } from "@prisma/client";
|
||||
import { TFnType } from "@tolgee/react";
|
||||
@@ -8,6 +7,7 @@ import { HTMLInputTypeAttribute } from "react";
|
||||
import { getLocalizedValue } from "@formbricks/lib/i18n/utils";
|
||||
import { surveyCache } from "@formbricks/lib/survey/cache";
|
||||
import { isConditionGroup } from "@formbricks/lib/surveyLogic/utils";
|
||||
import { getQuestionTypes } from "@formbricks/lib/utils/questions";
|
||||
import { recallToHeadline } from "@formbricks/lib/utils/recall";
|
||||
import { InvalidInputError } from "@formbricks/types/errors";
|
||||
import {
|
||||
|
||||
@@ -1,5 +1,5 @@
|
||||
import { authOptions } from "@/modules/auth/lib/authOptions";
|
||||
import { getContactAttributeKeys } from "@/modules/ee/contacts/lib/contact-attribute-keys";
|
||||
import { getContactAttributeKeys } from "@/modules/ee/contacts/lib/contacts";
|
||||
import { getSegments } from "@/modules/ee/contacts/segments/lib/segments";
|
||||
import { getIsContactsEnabled, getMultiLanguagePermission } from "@/modules/ee/license-check/lib/utils";
|
||||
import { getProjectPermissionByUserId } from "@/modules/ee/teams/lib/roles";
|
||||
|
||||
@@ -6,7 +6,6 @@ import {
|
||||
ZCreateSurveyFollowUpFormSchema,
|
||||
} from "@/modules/survey/editor/types/survey-follow-up";
|
||||
import FollowUpActionMultiEmailInput from "@/modules/survey/follow-ups/components/follow-up-action-multi-email-input";
|
||||
import { getQuestionIconMap } from "@/modules/survey/lib/questions";
|
||||
import { Button } from "@/modules/ui/components/button";
|
||||
import { Checkbox } from "@/modules/ui/components/checkbox";
|
||||
import { Editor } from "@/modules/ui/components/editor";
|
||||
@@ -39,6 +38,7 @@ import { useForm } from "react-hook-form";
|
||||
import toast from "react-hot-toast";
|
||||
import { TSurveyFollowUpAction, TSurveyFollowUpTrigger } from "@formbricks/database/types/survey-follow-up";
|
||||
import { getLocalizedValue } from "@formbricks/lib/i18n/utils";
|
||||
import { getQuestionIconMap } from "@formbricks/lib/utils/questions";
|
||||
import { recallToHeadline } from "@formbricks/lib/utils/recall";
|
||||
import { TSurvey, TSurveyQuestionTypeEnum } from "@formbricks/types/surveys/types";
|
||||
import { TUserLocale } from "@formbricks/types/user";
|
||||
|
||||
@@ -41,7 +41,6 @@ export const selectSurvey = {
|
||||
pin: true,
|
||||
resultShareKey: true,
|
||||
showLanguageSwitch: true,
|
||||
isBackButtonHidden: true,
|
||||
languages: {
|
||||
select: {
|
||||
default: true,
|
||||
|
||||
@@ -6,11 +6,19 @@ import { VerifyEmail } from "@/modules/survey/link/components/verify-email";
|
||||
import { getPrefillValue } from "@/modules/survey/link/lib/utils";
|
||||
import { SurveyInline } from "@/modules/ui/components/survey";
|
||||
import { Project, Response } from "@prisma/client";
|
||||
import { useTranslate } from "@tolgee/react";
|
||||
import { useSearchParams } from "next/navigation";
|
||||
import { useEffect, useMemo, useState } from "react";
|
||||
import { TResponseData, TResponseHiddenFieldValue } from "@formbricks/types/responses";
|
||||
import { FormbricksAPI } from "@formbricks/api";
|
||||
import { ResponseQueue } from "@formbricks/lib/responseQueue";
|
||||
import { SurveyState } from "@formbricks/lib/surveyState";
|
||||
import { TJsFileUploadParams } from "@formbricks/types/js";
|
||||
import { TResponseData, TResponseHiddenFieldValue, TResponseUpdate } from "@formbricks/types/responses";
|
||||
import { TUploadFileConfig } from "@formbricks/types/storage";
|
||||
import { TSurvey } from "@formbricks/types/surveys/types";
|
||||
|
||||
let setIsError = (_: boolean) => {};
|
||||
let setIsResponseSendingFinished = (_: boolean) => {};
|
||||
let setQuestionId = (_: string) => {};
|
||||
let setResponseData = (_: TResponseData) => {};
|
||||
|
||||
@@ -49,10 +57,15 @@ export const LinkSurvey = ({
|
||||
locale,
|
||||
isPreview,
|
||||
}: LinkSurveyProps) => {
|
||||
const { t } = useTranslate();
|
||||
const responseId = singleUseResponse?.id;
|
||||
const searchParams = useSearchParams();
|
||||
const skipPrefilled = searchParams.get("skipPrefilled") === "true";
|
||||
const sourceParam = searchParams.get("source");
|
||||
const suId = searchParams.get("suId");
|
||||
const defaultLanguageCode = survey.languages.find((surveyLanguage) => {
|
||||
return surveyLanguage.default;
|
||||
})?.language.code;
|
||||
|
||||
const startAt = searchParams.get("startAt");
|
||||
const isStartAtValid = useMemo(() => {
|
||||
@@ -71,8 +84,32 @@ export const LinkSurvey = ({
|
||||
return isValid;
|
||||
}, [survey, startAt]);
|
||||
|
||||
// pass in the responseId if the survey is a single use survey, ensures survey state is updated with the responseId
|
||||
let surveyState = useMemo(() => {
|
||||
return new SurveyState(survey.id, singleUseId, responseId);
|
||||
}, [survey.id, singleUseId, responseId]);
|
||||
|
||||
const prefillValue = getPrefillValue(survey, searchParams, languageCode);
|
||||
|
||||
const responseQueue = useMemo(
|
||||
() =>
|
||||
new ResponseQueue(
|
||||
{
|
||||
apiHost: webAppUrl,
|
||||
environmentId: survey.environmentId,
|
||||
retryAttempts: 2,
|
||||
onResponseSendingFailed: () => {
|
||||
setIsError(true);
|
||||
},
|
||||
onResponseSendingFinished: () => {
|
||||
// when response of current question is processed successfully
|
||||
setIsResponseSendingFinished(true);
|
||||
},
|
||||
},
|
||||
surveyState
|
||||
),
|
||||
[webAppUrl, survey.environmentId, surveyState]
|
||||
);
|
||||
const [autoFocus, setAutofocus] = useState(false);
|
||||
const hasFinishedSingleUseResponse = useMemo(() => {
|
||||
if (singleUseResponse?.finished) {
|
||||
@@ -111,7 +148,11 @@ export const LinkSurvey = ({
|
||||
}
|
||||
}, [survey.isVerifyEmailEnabled, verifiedEmail]);
|
||||
|
||||
if (hasFinishedSingleUseResponse) {
|
||||
useEffect(() => {
|
||||
responseQueue.updateSurveyState(surveyState);
|
||||
}, [responseQueue, surveyState]);
|
||||
|
||||
if (!surveyState.isResponseFinished() && hasFinishedSingleUseResponse) {
|
||||
return <SurveyLinkUsed singleUseMessage={survey.singleUse} />;
|
||||
}
|
||||
|
||||
@@ -170,14 +211,81 @@ export const LinkSurvey = ({
|
||||
PRIVACY_URL={PRIVACY_URL}
|
||||
isBrandingEnabled={project.linkSurveyBranding}>
|
||||
<SurveyInline
|
||||
apiHost={!isPreview ? webAppUrl : undefined}
|
||||
environmentId={!isPreview ? survey.environmentId : undefined}
|
||||
survey={survey}
|
||||
styling={determineStyling()}
|
||||
languageCode={languageCode}
|
||||
isBrandingEnabled={project.linkSurveyBranding}
|
||||
shouldResetQuestionId={false}
|
||||
onFileUpload={isPreview ? async (file) => `https://formbricks.com/${file.name}` : undefined}
|
||||
getSetIsError={(f: (value: boolean) => void) => {
|
||||
setIsError = f;
|
||||
}}
|
||||
getSetIsResponseSendingFinished={
|
||||
!isPreview
|
||||
? (f: (value: boolean) => void) => {
|
||||
setIsResponseSendingFinished = f;
|
||||
}
|
||||
: undefined
|
||||
}
|
||||
onRetry={() => {
|
||||
setIsError(false);
|
||||
void responseQueue.processQueue();
|
||||
}}
|
||||
onDisplay={() => {
|
||||
if (!isPreview) {
|
||||
void (async () => {
|
||||
const api = new FormbricksAPI({
|
||||
apiHost: webAppUrl,
|
||||
environmentId: survey.environmentId,
|
||||
});
|
||||
|
||||
const res = await api.client.display.create({
|
||||
surveyId: survey.id,
|
||||
});
|
||||
|
||||
if (!res.ok) {
|
||||
throw new Error(t("s.could_not_create_display"));
|
||||
}
|
||||
|
||||
const { id } = res.data;
|
||||
|
||||
surveyState.updateDisplayId(id);
|
||||
responseQueue.updateSurveyState(surveyState);
|
||||
})();
|
||||
}
|
||||
}}
|
||||
onResponse={(responseUpdate: TResponseUpdate) => {
|
||||
!isPreview &&
|
||||
responseQueue.add({
|
||||
data: {
|
||||
...responseUpdate.data,
|
||||
...hiddenFieldsRecord,
|
||||
...getVerifiedEmail,
|
||||
},
|
||||
ttc: responseUpdate.ttc,
|
||||
finished: responseUpdate.finished,
|
||||
endingId: responseUpdate.endingId,
|
||||
language:
|
||||
responseUpdate.language === "default" && defaultLanguageCode
|
||||
? defaultLanguageCode
|
||||
: responseUpdate.language,
|
||||
meta: {
|
||||
url: window.location.href,
|
||||
source: typeof sourceParam === "string" ? sourceParam : "",
|
||||
},
|
||||
variables: responseUpdate.variables,
|
||||
displayId: surveyState.displayId,
|
||||
...(Object.keys(hiddenFieldsRecord).length > 0 && { hiddenFields: hiddenFieldsRecord }),
|
||||
});
|
||||
}}
|
||||
onFileUpload={async (file: TJsFileUploadParams["file"], params: TUploadFileConfig) => {
|
||||
const api = new FormbricksAPI({
|
||||
apiHost: webAppUrl,
|
||||
environmentId: survey.environmentId,
|
||||
});
|
||||
|
||||
const uploadedUrl = await api.client.storage.uploadFile(file, params);
|
||||
return uploadedUrl;
|
||||
}}
|
||||
// eslint-disable-next-line jsx-a11y/no-autofocus -- need it as focus behaviour is different in normal surveys and survey preview
|
||||
autoFocus={autoFocus}
|
||||
prefillResponseData={prefillValue}
|
||||
@@ -191,13 +299,7 @@ export const LinkSurvey = ({
|
||||
}}
|
||||
startAtQuestionId={startAt && isStartAtValid ? startAt : undefined}
|
||||
fullSizeCards={isEmbed}
|
||||
hiddenFieldsRecord={{
|
||||
...hiddenFieldsRecord,
|
||||
...getVerifiedEmail,
|
||||
}}
|
||||
singleUseId={singleUseId}
|
||||
singleUseResponseId={responseId}
|
||||
getSetIsResponseSendingFinished={(_f: (value: boolean) => void) => {}}
|
||||
hiddenFieldsRecord={hiddenFieldsRecord}
|
||||
/>
|
||||
</LinkSurveyWrapper>
|
||||
);
|
||||
|
||||
@@ -41,5 +41,4 @@ export const getMinimalSurvey = (t: TFnType): TSurvey => ({
|
||||
isSingleResponsePerEmailEnabled: false,
|
||||
variables: [],
|
||||
followUps: [],
|
||||
isBackButtonHidden: false,
|
||||
});
|
||||
|
||||
@@ -1,6 +1,5 @@
|
||||
"use client";
|
||||
|
||||
import { getQuestionIconMap } from "@/modules/survey/lib/questions";
|
||||
import { Switch } from "@/modules/ui/components/switch";
|
||||
import { useSortable } from "@dnd-kit/sortable";
|
||||
import { CSS } from "@dnd-kit/utilities";
|
||||
@@ -9,6 +8,7 @@ import { useTranslate } from "@tolgee/react";
|
||||
import { capitalize } from "lodash";
|
||||
import { GripVertical } from "lucide-react";
|
||||
import { getLocalizedValue } from "@formbricks/lib/i18n/utils";
|
||||
import { getQuestionIconMap } from "@formbricks/lib/utils/questions";
|
||||
import { TSurvey } from "@formbricks/types/surveys/types";
|
||||
|
||||
interface DataTableSettingsModalItemProps<T> {
|
||||
|
||||
@@ -1,21 +1,20 @@
|
||||
import { useCallback, useEffect, useMemo, useState } from "react";
|
||||
import { SurveyContainerProps } from "@formbricks/types/formbricks-surveys";
|
||||
import { SurveyInlineProps, SurveyModalProps } from "@formbricks/types/formbricks-surveys";
|
||||
|
||||
const createContainerId = () => `formbricks-survey-container`;
|
||||
declare global {
|
||||
interface Window {
|
||||
formbricksSurveys: {
|
||||
renderSurveyInline: (props: SurveyContainerProps) => void;
|
||||
renderSurveyModal: (props: SurveyContainerProps) => void;
|
||||
renderSurvey: (props: SurveyContainerProps) => void;
|
||||
renderSurveyInline: (props: SurveyInlineProps) => void;
|
||||
renderSurveyModal: (props: SurveyModalProps) => void;
|
||||
};
|
||||
}
|
||||
}
|
||||
|
||||
export const SurveyInline = (props: Omit<SurveyContainerProps, "containerId">) => {
|
||||
export const SurveyInline = (props: Omit<SurveyInlineProps, "containerId">) => {
|
||||
const containerId = useMemo(() => createContainerId(), []);
|
||||
const renderInline = useCallback(
|
||||
() => window.formbricksSurveys.renderSurvey({ ...props, containerId, mode: "inline" }),
|
||||
() => window.formbricksSurveys.renderSurveyInline({ ...props, containerId }),
|
||||
[containerId, props]
|
||||
);
|
||||
const [isScriptLoaded, setIsScriptLoaded] = useState(false);
|
||||
|
||||
@@ -1,6 +1,6 @@
|
||||
{
|
||||
"name": "@formbricks/web",
|
||||
"version": "3.3.1",
|
||||
"version": "3.2.0",
|
||||
"private": true,
|
||||
"scripts": {
|
||||
"clean": "rimraf .turbo node_modules .next",
|
||||
@@ -15,7 +15,6 @@
|
||||
},
|
||||
"dependencies": {
|
||||
"@ai-sdk/azure": "1.1.9",
|
||||
"@boxyhq/saml-jackson": "1.37.1",
|
||||
"@dnd-kit/core": "6.3.1",
|
||||
"@dnd-kit/modifiers": "9.0.0",
|
||||
"@dnd-kit/sortable": "10.0.0",
|
||||
|
||||
@@ -29,7 +29,6 @@ test.describe("JS Package Test", async () => {
|
||||
let server: http.Server;
|
||||
let environmentId: string;
|
||||
|
||||
test.setTimeout(3 * 60 * 1000);
|
||||
test.beforeAll(async () => {
|
||||
// Create a simple HTTP server
|
||||
server = http.createServer((_, res) => {
|
||||
@@ -125,7 +124,6 @@ test.describe("JS Package Test", async () => {
|
||||
|
||||
await page.getByTestId("loading-spinner").waitFor({ state: "hidden" });
|
||||
await page.waitForLoadState("networkidle");
|
||||
await page.waitForTimeout(5000);
|
||||
|
||||
// Validate displays and response
|
||||
await page.goto("/");
|
||||
@@ -133,7 +131,7 @@ test.describe("JS Package Test", async () => {
|
||||
await page.getByRole("link", { name: "product Market Fit (Superhuman)" }).click();
|
||||
await page.waitForSelector("text=Responses");
|
||||
await page.waitForLoadState("networkidle");
|
||||
await page.waitForTimeout(5000);
|
||||
await page.waitForTimeout(2000);
|
||||
|
||||
const impressionsCount = await page.getByRole("button", { name: "Impressions" }).innerText();
|
||||
expect(impressionsCount).toEqual("Impressions\n\n1");
|
||||
|
||||
@@ -3,18 +3,9 @@
|
||||
import { TolgeeProvider, TolgeeStaticData } from "@tolgee/react";
|
||||
import { useRouter } from "next/navigation";
|
||||
import { useEffect } from "react";
|
||||
import branch from "../../../branch.json";
|
||||
import { TolgeeBase } from "./shared";
|
||||
|
||||
// Try to import branch.json, but handle the case where it doesn't exist
|
||||
let branchName: string | undefined;
|
||||
try {
|
||||
const branch = require("../../../branch.json");
|
||||
branchName = branch.branchName;
|
||||
} catch (e) {
|
||||
// File doesn't exist in production, so we'll use undefined
|
||||
branchName = undefined;
|
||||
}
|
||||
|
||||
type Props = {
|
||||
language: string;
|
||||
staticData: TolgeeStaticData;
|
||||
@@ -22,7 +13,7 @@ type Props = {
|
||||
};
|
||||
|
||||
const tolgee = TolgeeBase().init({
|
||||
tagNewKeys: branchName ? [`draft:${branchName}`] : [],
|
||||
tagNewKeys: [`draft:${branch.branchName}`],
|
||||
});
|
||||
|
||||
export const TolgeeNextProvider = ({ language, staticData, children }: Props) => {
|
||||
|
||||
@@ -1,22 +1,13 @@
|
||||
import { createServerInstance } from "@tolgee/react/server";
|
||||
import branch from "../../../branch.json";
|
||||
import { getLocale } from "./language";
|
||||
import { TolgeeBase } from "./shared";
|
||||
|
||||
// Try to import branch.json, but handle the case where it doesn't exist
|
||||
let branchName: string | undefined;
|
||||
try {
|
||||
const branch = require("../../../branch.json");
|
||||
branchName = branch.branchName;
|
||||
} catch (e) {
|
||||
// File doesn't exist in production, so we'll use undefined
|
||||
branchName = undefined;
|
||||
}
|
||||
|
||||
export const { getTolgee, getTranslate, T } = createServerInstance({
|
||||
getLocale: getLocale,
|
||||
createTolgee: async (language) => {
|
||||
return TolgeeBase().init({
|
||||
tagNewKeys: branchName ? [`draft:${branchName}`] : [],
|
||||
tagNewKeys: [`draft:${branch.branchName}`],
|
||||
observerOptions: {
|
||||
fullKeyEncode: true,
|
||||
},
|
||||
|
||||
@@ -1,9 +1,5 @@
|
||||
{
|
||||
"functions": {
|
||||
"app/**/*.ts": {
|
||||
"maxDuration": 10,
|
||||
"memory": 512
|
||||
},
|
||||
"app/api/cron/**/*.ts": {
|
||||
"maxDuration": 180,
|
||||
"memory": 512
|
||||
@@ -11,6 +7,10 @@
|
||||
"app/api/v1/client/**/*.ts": {
|
||||
"maxDuration": 10,
|
||||
"memory": 200
|
||||
},
|
||||
"app/**/*.ts": {
|
||||
"maxDuration": 10,
|
||||
"memory": 512
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
1
branch.json
Normal file
1
branch.json
Normal file
@@ -0,0 +1 @@
|
||||
{"branchName": "473-weekly-summary-not-working"}
|
||||
@@ -111,9 +111,6 @@ x-environment: &environment
|
||||
# OIDC_DISPLAY_NAME:
|
||||
# OIDC_SIGNING_ALGORITHM:
|
||||
|
||||
# Set the below to SAML Provider if you want to enable SAML
|
||||
# SAML_DATABASE_URL: "postgresql://postgres:postgres@postgres:5432/formbricks-saml?sslmode=disable"
|
||||
|
||||
########################################## OPTIONAL (THIRD PARTY INTEGRATIONS) ###########################################
|
||||
|
||||
# Oauth credentials for Notion Integration
|
||||
@@ -188,11 +185,9 @@ services:
|
||||
- 3000:3000
|
||||
volumes:
|
||||
- uploads:/home/nextjs/apps/web/uploads/
|
||||
- ./saml-connection:/home/nextjs/apps/web/saml-connection
|
||||
<<: *environment
|
||||
|
||||
volumes:
|
||||
postgres:
|
||||
driver: local
|
||||
uploads:
|
||||
driver: local
|
||||
|
||||
@@ -1,44 +0,0 @@
|
||||
---
|
||||
title: "Generate API Key"
|
||||
icon: "key"
|
||||
description: "Here is how you can generate an API key which gives you full access to the Formbricks Management API. Keep it safe!"
|
||||
---
|
||||
<Note>
|
||||
As of now, API keys are located in the Project Configuration page. We are moving them to the Organization Settings page in the upcoming release. For you, nothing will change.
|
||||
</Note>
|
||||
|
||||
## Generate API key
|
||||
|
||||
<Steps>
|
||||
<Step title="Navigate to 'Configuration'">
|
||||
Go to the Configuration page of your project:
|
||||

|
||||
</Step>
|
||||
|
||||
<Step title="Access 'API Keys' tab">
|
||||
Click on the **API Keys** tab.
|
||||
</Step>
|
||||
|
||||
<Step title="Generate key">
|
||||
Decide if you want to generate a key for the development or production environment. If you want to switch environemnts you can do so in the top right corner. Click on the corresponding button.
|
||||
</Step>
|
||||
|
||||
<Step title="Add a label to your key">
|
||||
Add a label to your key to help you identify it.
|
||||

|
||||
</Step>
|
||||
|
||||
<Step title="Copy your key">
|
||||
Copy the API key and save it in a secure location. You won't be able to see it again.
|
||||
<Note>
|
||||
Store API key safely! Anyone who has your API key has full control over your
|
||||
account. For security reasons, you cannot view the API key again.
|
||||
</Note>
|
||||
</Step>
|
||||
</Steps>
|
||||
|
||||
## Delete API key
|
||||
|
||||
- On **Configuration** > **API Keys** page, find the key you wish to revoke and select “Delete”.
|
||||
|
||||
- Your API key will stop working immediately.
|
||||
14
docs/api-reference/introduction.mdx
Normal file
14
docs/api-reference/introduction.mdx
Normal file
@@ -0,0 +1,14 @@
|
||||
---
|
||||
title: "API v1.0.0"
|
||||
icon: "code-compare"
|
||||
---
|
||||
|
||||
Formbricks offers two types of APIs: the **Public Client API** and the **Management API**. Each API serves a different purpose, has *different* authentication requirements, and provides access to different data and settings.
|
||||
|
||||
### API Key Setup
|
||||
|
||||
Checkout the [API Key Setup](/api-reference/rest-api) to access the Management APIs with an API Key.
|
||||
|
||||
If you’ve forked the collection and are running it, update the `apiKey` and `environmentId` in the collection variables with your values. We also provide post-run scripts to help auto-assign variables when running scripts.
|
||||
|
||||
Need more help? Visit our [Website](https://formbricks.com/) or join our [Discord](https://formbricks.com/discord)!
|
||||
@@ -7725,7 +7725,7 @@
|
||||
}
|
||||
},
|
||||
"summary": "Health Check",
|
||||
"tags": ["Health"]
|
||||
"tags": ["default"]
|
||||
}
|
||||
}
|
||||
},
|
||||
|
||||
@@ -5,8 +5,9 @@ description: "
|
||||
Formbricks provides two APIs: the Public Client API for frontend survey interactions and the Management API for backend management tasks."
|
||||
---
|
||||
|
||||
Formbricks offers two types of APIs: the **Public Client API** and the **Management API**. Each API serves a different purpose, has *different* authentication requirements, and provides access to different data and settings.
|
||||
|
||||
<Info>
|
||||
View our [API Documentation](/api-reference) in more than 30 frameworks and languages.
|
||||
</Info>
|
||||
|
||||
## Public Client API
|
||||
|
||||
@@ -16,7 +17,7 @@ We currently have the following Client API methods exposed and below is their do
|
||||
|
||||
- [Displays API](/api-reference/client-api->-display/create-display) - Mark a survey as displayed or link a display to a response for a person.
|
||||
|
||||
- [Contacts API](/api-reference/client-api->-contacts/update-contact-attributes) - Update contact attributes.
|
||||
- [People API](/api-reference/client-api->-people/create-person) - Create & Update a Person (e.g., attributes, email, userId, etc.)
|
||||
|
||||
- [Responses API](/api-reference/client-api->-response/create-response) - Create & Update a Response for a Survey.
|
||||
|
||||
@@ -40,7 +41,88 @@ We currently have the following Management API methods exposed and below is thei
|
||||
|
||||
- [Webhook API](/api-reference/management-api->-webhook/get-all-webhooks) - List, Create, and Delete Webhooks
|
||||
|
||||
## How to Generate an API key
|
||||
|
||||
API requests require a personal API key for authorization. This API key gives you the same rights as if you were logged in at Formbricks UI - **keep it private!**
|
||||
|
||||
- Go to your settings on [Formbricks UI](https://app.formbricks.com).
|
||||
|
||||
- Go to page “API keys”
|
||||
|
||||
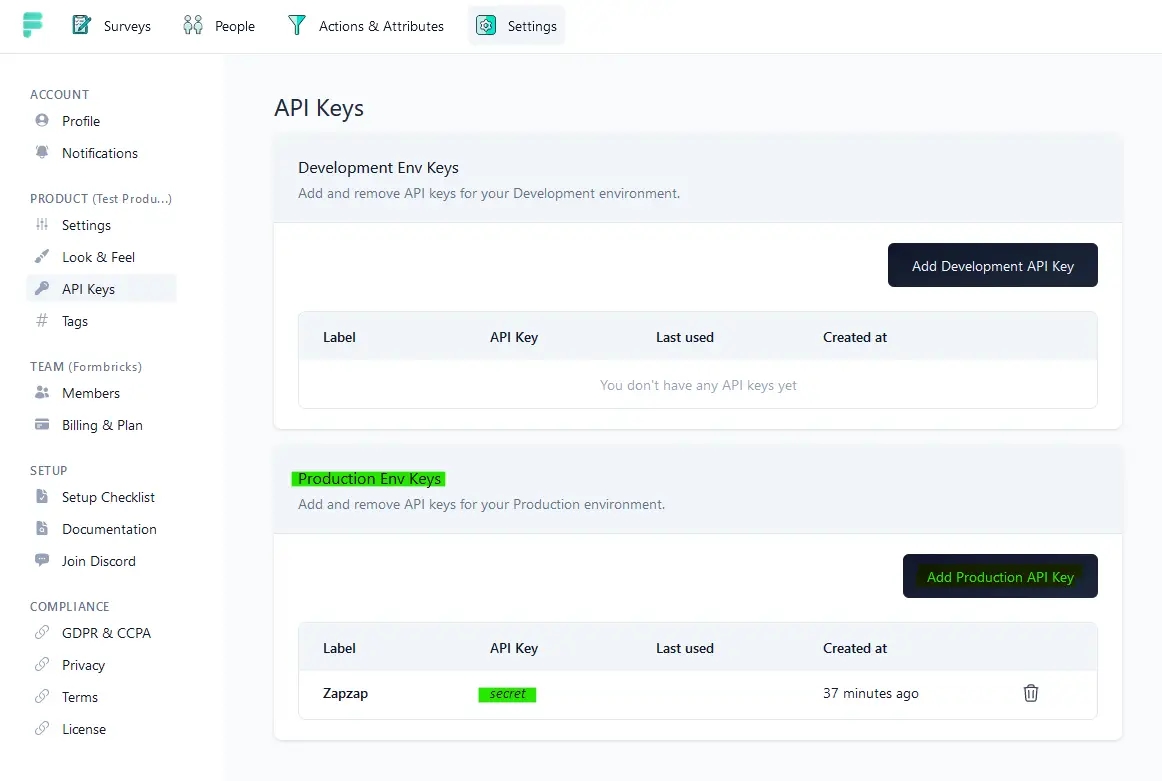
|
||||
|
||||
- Create a key for the development or production environment.
|
||||
|
||||
- Copy the key immediately. You won’t be able to see it again.
|
||||
|
||||
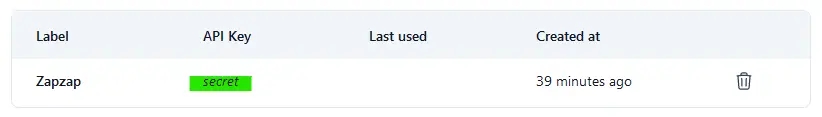
|
||||
|
||||
<Note>
|
||||
**Store API key safely! Anyone who has your API key has full control over your
|
||||
account. For security reasons, you cannot view the API key again.**
|
||||
</Note>
|
||||
|
||||
## Test your API Key
|
||||
|
||||
Hit the below request to verify that you are authenticated with your API Key and the server is responding.
|
||||
|
||||
### Get My Profile
|
||||
|
||||
Get the project details and environment type of your account.
|
||||
|
||||
### Mandatory Headers
|
||||
|
||||
| Name | x-Api-Key |
|
||||
| --------------- | ------------------------ |
|
||||
| **Type** | string |
|
||||
| **Description** | Your Formbricks API key. |
|
||||
|
||||
### Request
|
||||
|
||||
```bash cURL
|
||||
GET - /api/v1/me
|
||||
|
||||
curl --location \
|
||||
'https://app.formbricks.com/api/v1/me' \
|
||||
--header \
|
||||
'x-api-key: <your-api-key>'
|
||||
```
|
||||
|
||||
### Response
|
||||
|
||||
<CodeGroup>
|
||||
|
||||
|
||||
```bash 200 (Success)
|
||||
{
|
||||
"id": "cll2m30r70004mx0huqkitgqv",
|
||||
"createdAt": "2023-08-08T18:04:59.922Z",
|
||||
"updatedAt": "2023-08-08T18:04:59.922Z",
|
||||
"type": "production",
|
||||
"project": {
|
||||
"id": "cll2m30r60003mx0hnemjfckr",
|
||||
"name": "My Project"
|
||||
},
|
||||
"appSetupCompleted": false,
|
||||
"websiteSetupCompleted": false,
|
||||
}
|
||||
```
|
||||
|
||||
```bash 401 (Not Authenticated)
|
||||
Not authenticated
|
||||
```
|
||||
</CodeGroup>
|
||||
|
||||
|
||||
### Delete a personal API key
|
||||
|
||||
- Go to settings on [app.formbricks.com](https://app.formbricks.com/).
|
||||
|
||||
- Go to the page “API keys”.
|
||||
|
||||
- Find the key you wish to revoke and select “Delete”.
|
||||
|
||||
- Your API key will stop working immediately.
|
||||
|
||||
---
|
||||
|
||||
|
||||
@@ -1,50 +0,0 @@
|
||||
---
|
||||
title: "Test API Key"
|
||||
icon: "message-check"
|
||||
description: "Here is how you can test your API key to make sure it is working."
|
||||
---
|
||||
|
||||
To test if your API key is working, you can use the following request:
|
||||
|
||||
### Mandatory Headers
|
||||
|
||||
| Name | x-Api-Key |
|
||||
| --------------- | ------------------------ |
|
||||
| **Type** | string |
|
||||
| **Description** | Your Formbricks API key. |
|
||||
|
||||
### Request
|
||||
|
||||
```bash cURL
|
||||
GET - /api/v1/me
|
||||
|
||||
curl --location \
|
||||
'https://app.formbricks.com/api/v1/me' \
|
||||
--header \
|
||||
'x-api-key: <your-api-key>'
|
||||
```
|
||||
|
||||
### Response
|
||||
|
||||
<CodeGroup>
|
||||
|
||||
|
||||
```bash 200 (Success)
|
||||
{
|
||||
"id": "cll2m30r70004mx0huqkitgqv",
|
||||
"createdAt": "2023-08-08T18:04:59.922Z",
|
||||
"updatedAt": "2023-08-08T18:04:59.922Z",
|
||||
"type": "production",
|
||||
"project": {
|
||||
"id": "cll2m30r60003mx0hnemjfckr",
|
||||
"name": "My Project"
|
||||
},
|
||||
"appSetupCompleted": false,
|
||||
"websiteSetupCompleted": false,
|
||||
}
|
||||
```
|
||||
|
||||
```bash 401 (Not Authenticated)
|
||||
Not authenticated
|
||||
```
|
||||
</CodeGroup>
|
||||
@@ -1,11 +1,11 @@
|
||||
---
|
||||
title: "Setup SAML with Identity Providers"
|
||||
description: "This guide explains the settings you need to use to configure SAML with your Identity Provider. Once configured, obtain an XML metadata file and use it to configure SAML in Formbricks."
|
||||
description: "This guide explains the settings you need to use to configure SAML with your Identity Provider. Once configured, obtain an XML metadata file and upload it on your Formbricks instance."
|
||||
---
|
||||
|
||||
### SAML Registration with Identity Providers
|
||||
|
||||
This guide explains the settings you need to use to configure SAML with your Identity Provider. Once configured, obtain an XML metadata file and use it to configure SAML in Formbricks.
|
||||
This guide explains the settings you need to use to configure SAML with your Identity Provider. Once configured, obtain an XML metadata file and upload it on your Formbricks instance.
|
||||
|
||||
> **Note:** Please do not add a trailing slash at the end of the URLs. Create them exactly as shown below.
|
||||
|
||||
@@ -23,13 +23,13 @@ This guide explains the settings you need to use to configure SAML with your Ide
|
||||
|
||||
**Mapping Attributes / Attribute Statements:**
|
||||
|
||||
- [http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier](http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier) -> id
|
||||
* [http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier](http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier) -> id
|
||||
|
||||
- [http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress](http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress) -> email
|
||||
* [http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress](http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress) -> email
|
||||
|
||||
- [http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname](http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname) -> firstName
|
||||
* [http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname](http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname) -> firstName
|
||||
|
||||
- [http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname](http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname) -> lastName
|
||||
* [http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname](http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname) -> lastName
|
||||
|
||||
### SAML With Okta
|
||||
|
||||
@@ -38,47 +38,57 @@ This guide explains the settings you need to use to configure SAML with your Ide
|
||||
For example, in Okta, once you create an account, you can click on Applications on the sidebar menu:
|
||||
|
||||
<img src="/images/development/guides/auth-and-provision/okta/okta-applications.webp" />
|
||||
</Step>
|
||||
|
||||
</Step>
|
||||
<Step title="Click on Create App Integration">
|
||||
<img src="/images/development/guides/auth-and-provision/okta/create-app-integration.webp" />
|
||||
<img src="/images/development/guides/auth-and-provision/okta/create-app-integration.webp" />
|
||||
</Step>
|
||||
|
||||
<Step title="Select SAML 2.0 in the modal form, and click Next">
|
||||
<img src="/images/development/guides/auth-and-provision/okta/select-saml-2.0.webp" />
|
||||
</Step>
|
||||
|
||||
<Step title="Fill the general settings as shown and click Next">
|
||||
<img src="/images/development/guides/auth-and-provision/okta/general-settings.webp" />
|
||||
</Step>
|
||||
<Step title="Enter the SAML Integration Settings as shown and click Next">
|
||||
- **Single Sign-On URL**: `https://<your-formbricks-instance>/api/auth/saml/callback` or `http://localhost:3000/api/auth/saml/callback` (if you are running Formbricks locally)
|
||||
- **Audience URI (SP Entity ID)**: `https://saml.formbricks.com`
|
||||
<img src="/images/development/guides/auth-and-provision/okta/saml-integration-settings.webp" />
|
||||
</Step>
|
||||
|
||||
<Step title="Fill the fields mapping as shown and click Next">
|
||||
<img src="/images/development/guides/auth-and-provision/okta/fields-mapping.webp" />
|
||||
</Step>
|
||||
|
||||
<Step title="Enter the SAML Integration Settings as shown and click Next">
|
||||
<img src="/images/development/guides/auth-and-provision/okta/saml-integration-settings.webp" />
|
||||
</Step>
|
||||
|
||||
<Step title="Check the internal app checkbox and click Finish">
|
||||
<img src="/images/development/guides/auth-and-provision/okta/internal-app.webp" />
|
||||
</Step>
|
||||
|
||||
<Step title="Check that the app is created successfully">
|
||||
<img src="/images/development/guides/auth-and-provision/okta/app-created.webp" />
|
||||
</Step>
|
||||
|
||||
<Step title="Click on the app and head over to the Assignments tab">
|
||||
<img src="/images/development/guides/auth-and-provision/okta/assignments-tab.webp" />
|
||||
</Step>
|
||||
|
||||
<Step title="Click on Assign button and select Assign to People">
|
||||
<img src="/images/development/guides/auth-and-provision/okta/assign-to-people.webp" />
|
||||
</Step>
|
||||
|
||||
<Step title="Select the users you want to assign the app to and click Assign">
|
||||
<img src="/images/development/guides/auth-and-provision/okta/select-users.webp" />
|
||||
</Step>
|
||||
<Step title="Head over to the Sign On tab and click on the 'view SAML setup instructions' button">
|
||||
<img src="/images/development/guides/auth-and-provision/okta/view-saml-instructions.webp" />
|
||||
|
||||
<Step title="Head over to the Sign On tab and scroll to the bottom to get the metadata, click on the Actions button">
|
||||
<img src="/images/development/guides/auth-and-provision/okta/actions-button.webp" />
|
||||
</Step>
|
||||
<Step title="Scroll to the bottom and copy the IDP metadata">
|
||||
<img src="/images/development/guides/auth-and-provision/okta/idp-metadata.webp" />
|
||||
|
||||
<Step title="Click on View IdP metadata">
|
||||
<img src="/images/development/guides/auth-and-provision/okta/view-idp-metadata.webp" />
|
||||
</Step>
|
||||
<Step title="Copy the IDP metadata and paste it in the `connection.xml` file in the `formbricks/saml-connection` directory" />
|
||||
|
||||
<Step title="Copy the metadata and paste it in the Formbricks SAML configuration" />
|
||||
</Steps>
|
||||
|
||||
That's it. Now when you try to login with SSO, your application on Okta will handle the authentication.
|
||||
That's it. Now when you try to login with SSO, your application on Okta will handle the authentication.
|
||||
Binary file not shown.
|
Before Width: | Height: | Size: 42 KiB |
Binary file not shown.
|
Before Width: | Height: | Size: 19 KiB |
Binary file not shown.
|
After Width: | Height: | Size: 21 KiB |
Binary file not shown.
|
Before Width: | Height: | Size: 50 KiB |
Binary file not shown.
|
After Width: | Height: | Size: 23 KiB |
Binary file not shown.
|
Before Width: | Height: | Size: 111 KiB |
Some files were not shown because too many files have changed in this diff Show More
Reference in New Issue
Block a user